Lieberman RED Identity Management
Author: e | 2025-04-23

BeyondTrust Privileged Identity (formerly Lieberman RED Identity Management) is a password management solution that helps companies secure, manage, and administer credentials for privileged users and IT vendors. Integrate BeyondTrust Privileged Identity (Lieberman RED Identity Management) with Axonius Asset Management Platform. BeyondTrust Privileged Identity (formerly Lieberman RED Identity Management) is a password management solution that helps companies secure, manage, and administer credentials for privileged users and IT vendors. Integrate BeyondTrust Privileged Identity (Lieberman RED Identity Management) with Axonius Asset Management Platform.
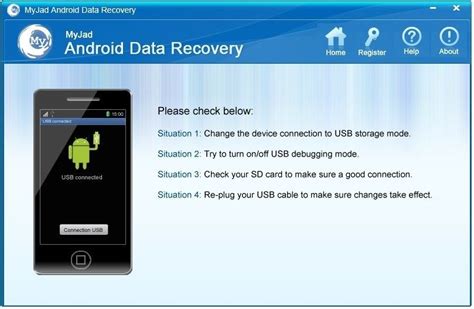
Case Study: Lieberman RED Identity Management
Likelihood to RecommendBeyondTrustWorks great in a Wiindows/Linux environments. Easy to roll out and especially easy to update. Account manager stays in touch often. Monthly training on the product is a plus.Read full reviewCyberarkThe system is great for enterprise or larger IT departments or teams where temporary or full access may be given using privileged IDs. Requirements for needing local admin access is also eliminated which can help with specific Windows workstation related tasks. It can be very useful when working with remote teams or contractors who may need temporary access to a system when required.Read full reviewProsBeyondTrustManage local accounts of workstations and servers.The web interface is easy for users of RED to use.The shared password list is a very nice feature that allows users to store credentials that have to remain static.Read full reviewCyberarkAutomatically discover new servers on the network and take control of the local admin password by vaulting it and ensuring nobody knows the password. A different password on every server.Automatically roll the password in a configurable manner - after each use, after a certain period of time, etc.Track and govern sensitive account usage by ensuring only properly authorized users can access the vault and obtain the credentials and then monitor usage.Verified UserAnonymousRead full reviewConsBeyondTrustNot as slick as CyberArkTraining is free, but could use a lot of improvementDocumentation needs refinementRead full reviewCyberarkGUI - right now everything is on one page/dashboard. Some level of folder/Safe type view would be greatMore options when storing passwords - especially for network based passwordsBetter integrations with vendors like Cisco so that admins dont need to really get the password from the vault (think Last Pass type add on)Verified UserAnonymousRead full reviewSupport RatingBeyondTrustCyberarkCustomer support and technical support have always been great when we require assistance. Especially when we come across issues that we're not familiar with.Read full reviewAlternatives ConsideredBeyondTrustCyberARK is superior in every way. Lieberman RED was selected by upper management without consulting with technical employees Read full reviewCyberarkIt is known as one of the safest products in the market. It has good support and is also available as on-premise. You can run it BeyondTrust Privileged Identity (formerly Lieberman RED Identity Management) is a password management solution that helps companies secure, manage, and administer credentials for privileged users and IT vendors. Integrate BeyondTrust Privileged Identity (Lieberman RED Identity Management) with Axonius Asset Management Platform. Likelihood to RecommendBeyondTrustWorks great in a Wiindows/Linux environments. Easy to roll out and especially easy to update. Account manager stays in touch often. Monthly training on the product is a plus.Read full reviewBroadcomCb Protect is best suited somewhere where you want to maximize the lockdown of workstations. So moving past no local admin rights to blocking specific applications and peripherals. The idea would be to have a list of applications you want to run, and then anything else is not able to be used. As stated prior, if you have a very fluid environment where you are having all sorts of new applications installed frequently (I feel for you!!) this is still do-able, but it misses the general idea. I think especially in environments that are more sensitive to new applications, like banks, healthcare systems etc, this is a good fit. The ability to look at application levels, drift, unapproved software etc is very useful.Read full reviewProsBeyondTrustManage local accounts of workstations and servers.The web interface is easy for users of RED to use.The shared password list is a very nice feature that allows users to store credentials that have to remain static.Read full reviewBroadcomControls file writes, executions of the scriptsDefends from process injections, memory protectionVisibility and lock down posibilitiesVerified UserAnonymousRead full reviewConsBeyondTrustNot as slick as CyberArkTraining is free, but could use a lot of improvementDocumentation needs refinementRead full reviewBroadcomPerhaps more specific training.Read full reviewAlternatives ConsideredBeyondTrustCyberARK is superior in every way. Lieberman RED was selected by upper management without consulting with technical employees Read full reviewBroadcomThe big difference between Protect and Barkly/AMP is how exactly it goes about what it's doing. Protect is application whitelisting and program reputation. So the way it's protecting you is using a proprietary reputation service, and hash values to identify applications, and then hitting a list of whitelisted programs to decide if you are able to run that or not, based on the policy you are in. There is a LOT of value in that. We actually are working on transitioning to Cisco Advanced Malware Protection (AMP). The main reason is cost (about the same costComments
Likelihood to RecommendBeyondTrustWorks great in a Wiindows/Linux environments. Easy to roll out and especially easy to update. Account manager stays in touch often. Monthly training on the product is a plus.Read full reviewCyberarkThe system is great for enterprise or larger IT departments or teams where temporary or full access may be given using privileged IDs. Requirements for needing local admin access is also eliminated which can help with specific Windows workstation related tasks. It can be very useful when working with remote teams or contractors who may need temporary access to a system when required.Read full reviewProsBeyondTrustManage local accounts of workstations and servers.The web interface is easy for users of RED to use.The shared password list is a very nice feature that allows users to store credentials that have to remain static.Read full reviewCyberarkAutomatically discover new servers on the network and take control of the local admin password by vaulting it and ensuring nobody knows the password. A different password on every server.Automatically roll the password in a configurable manner - after each use, after a certain period of time, etc.Track and govern sensitive account usage by ensuring only properly authorized users can access the vault and obtain the credentials and then monitor usage.Verified UserAnonymousRead full reviewConsBeyondTrustNot as slick as CyberArkTraining is free, but could use a lot of improvementDocumentation needs refinementRead full reviewCyberarkGUI - right now everything is on one page/dashboard. Some level of folder/Safe type view would be greatMore options when storing passwords - especially for network based passwordsBetter integrations with vendors like Cisco so that admins dont need to really get the password from the vault (think Last Pass type add on)Verified UserAnonymousRead full reviewSupport RatingBeyondTrustCyberarkCustomer support and technical support have always been great when we require assistance. Especially when we come across issues that we're not familiar with.Read full reviewAlternatives ConsideredBeyondTrustCyberARK is superior in every way. Lieberman RED was selected by upper management without consulting with technical employees Read full reviewCyberarkIt is known as one of the safest products in the market. It has good support and is also available as on-premise. You can run it
2025-04-04Likelihood to RecommendBeyondTrustWorks great in a Wiindows/Linux environments. Easy to roll out and especially easy to update. Account manager stays in touch often. Monthly training on the product is a plus.Read full reviewBroadcomCb Protect is best suited somewhere where you want to maximize the lockdown of workstations. So moving past no local admin rights to blocking specific applications and peripherals. The idea would be to have a list of applications you want to run, and then anything else is not able to be used. As stated prior, if you have a very fluid environment where you are having all sorts of new applications installed frequently (I feel for you!!) this is still do-able, but it misses the general idea. I think especially in environments that are more sensitive to new applications, like banks, healthcare systems etc, this is a good fit. The ability to look at application levels, drift, unapproved software etc is very useful.Read full reviewProsBeyondTrustManage local accounts of workstations and servers.The web interface is easy for users of RED to use.The shared password list is a very nice feature that allows users to store credentials that have to remain static.Read full reviewBroadcomControls file writes, executions of the scriptsDefends from process injections, memory protectionVisibility and lock down posibilitiesVerified UserAnonymousRead full reviewConsBeyondTrustNot as slick as CyberArkTraining is free, but could use a lot of improvementDocumentation needs refinementRead full reviewBroadcomPerhaps more specific training.Read full reviewAlternatives ConsideredBeyondTrustCyberARK is superior in every way. Lieberman RED was selected by upper management without consulting with technical employees Read full reviewBroadcomThe big difference between Protect and Barkly/AMP is how exactly it goes about what it's doing. Protect is application whitelisting and program reputation. So the way it's protecting you is using a proprietary reputation service, and hash values to identify applications, and then hitting a list of whitelisted programs to decide if you are able to run that or not, based on the policy you are in. There is a LOT of value in that. We actually are working on transitioning to Cisco Advanced Malware Protection (AMP). The main reason is cost (about the same cost
2025-04-18Of the Monsters was unique and loved the design of the protagonist monster and the villain was beautiful Rated 5 out of 5 stars 06/09/24 Full Review CJ F Pretty good. Actually Rated 2.5 out of 5 stars 03/13/24 Full Review Joseph H This movie made my stomach "Rumble" and I threw up Rated 0.5 out of 5 stars 02/25/24 Full Review Read all reviews Read More Read Less POST RATING WRITE A REVIEW EDIT REVIEW Rumble: Movie Clip - The Gauntlet of Doom Rumble: Movie Clip - The Gauntlet of Doom 1:04 Rumble: Movie Clip - Do The Lift Rumble: Movie Clip - Do The Lift 1:05 View more videos Luca 91% 84% Luca Watchlist TRAILER for Luca Turning Red 95% 67% Turning Red Watchlist TRAILER for Turning Red Elemental 73% 93% Elemental Watchlist TRAILER for Elemental Hotel Transylvania 2 57% 64% Hotel Transylvania 2 Watchlist Hotel Transylvania 45% 72% Hotel Transylvania Watchlist Discover more movies and TV shows. View More Rumble: Trailer 1 Rumble: Trailer 1 1:42 View more videos Synopsis In a world where monster wrestling is a global sport and monsters are superstar athletes, teenage Winnie looks to follow in her father's footsteps by coaching a lovable underdog monster into a champion. Director Hamish Grieve Producer Mark Bakshi, Brad Booker Screenwriter Matt Lieberman, Hamish Grieve Production Co Paramount Pictures, WWE Studios, Good Universe, Reel FX Creative Studios, Paramount Animation, Walden Media Rating PG (Some Action and Rude Humor) Genre Kids & Family, Comedy, Fantasy, Animation Original Language English Release Date (Streaming) Dec 15, 2021 Runtime 1h 44m Sound Mix Dolby Atmos, Dolby Digital Aspect Ratio Scope (2.35:1) Most Popular at Home Now
2025-03-31Directed by Dennis Dugan ... (directed by) Writing Credits(WGA) Tim Herlihy ... (written by) & Adam Sandler ... (written by) Cast (in credits order) verified as complete Adam Sandler ... Happy Gilmore Christopher McDonald ... Shooter McGavin Julie Bowen ... Virginia Venit Frances Bay ... Grandma Carl Weathers ... Chubbs Allen Covert ... Otto Robert Smigel ... IRS Agent Bob Barker ... Bob Barker Richard Kiel ... Mr. Larson Dennis Dugan ... Doug Thompson Joe Flaherty ... Jeering Fan Lee Trevino ... Lee Trevino Kevin Nealon ... Potter Verne Lundquist ... Announcer Jared Van Snellenberg ... Happy's Waterbury Caddy Ken Camroux-Taylor ... Coach (as Ken Camroux) Rich Elwood ... Assistant Coach Nancy Hillis ... Terry (as Nancy McClure) Helena Yea ... Chinese Lady Will Sasso ... Mover (as William Sasso) Dee Jay Jackson ... Mover Ellie Harvie ... Registrar Ian Boothby ... Guy on Green Andrew Johnston ... Crowd Guy - Waterbury Kim Restell ... Crowd Girl - Waterbury (as Kimberley Restell) Fred Perron ... Waterbury Heckler Helen Honeywell ... Crazy Old Lady Paul Raskin ... Starter #1 - Waterbury William Samples ... Starter #2 - AT&T John Shaw ... Daniel Lafferty Ted Deekan ... Auctioneer (as Ted Deeken) John Destry ... Zamboni Driver James Crescenzo ... Shooter's AT&T Caddy (as Jim Crescenzo) Brett Armstrong ... Shooter's Tournament Caddy Peter Kelamis ... Potter's Caddy Stephen Tibbetts ... Pro Golfer Ed Lieberman ... Pro Golfer (as Edward Lieberman) Donnie MacMillan ... Young Happy Louis O'Donoghue ... Happy's Dad Lisanne Collett ...
2025-04-23NobodyThe custodia package has been removed The custodia package has been integrated into Red Hat Identity Management in RHEL 9 and is no longer shipped as a separate service. The gssntlmssp package has been removed As Windows New Technology LAN Manager (NTLM) is considered insecure, the gssntlmssp package has been removed. The nsslapd-conntablesize configuration parameter has been removed from 389-ds-base The nsslapd-conntablesize configuration parameter has been removed from the 389-ds-base package in RHEL 9.3. Previously, the nsslapd-conntablesize configuration attribute specified the size of the connection table that managed established connections. With the introduction of the multi-listener feature, which improves the management of established connections, Directory Server now calculates the size of the connection table dynamically. This also resolves issues, when the connection table size was set too low and it affected the number of connections the server was able to support. Starting with RHEL 9.3, use only nsslapd-maxdescriptors and nsslapd-reservedescriptors attributes to manage the number of TCP/IP connections Directory Server can support. Limited support for FreeRADIUS In RHEL 9, the following external authentication modules are not supported as part of the FreeRADIUS offering: The MySQL, PostgreSQL, SQlite, and unixODBC database connectors The Perl language module The REST API module The PAM authentication module and other authentication modules that are provided as part of the base package are not affected. You can find replacements for the removed modules in community-supported packages, for example in the Fedora project. In addition, the scope of support for the freeradius package is now limited to the following use cases: Using FreeRADIUS as an authentication provider with Identity Management (IdM) as the backend source of authentication. The authentication is happening through the krb5 and LDAP authentication packages or as PAM authentication in the main FreeRADIUS package. Using FreeRADIUS to provide a source-of-truth for authentication in IdM, through the Python 3 authentication package. In contrast to these removals, Red Hat is now strengthening its support of the following external authentication modules with FreeRADIUS: Authentication based on krb5 and LDAP Python 3 authentication The focus on these integration options is in close alignment with the strategic direction of Red Hat IdM. The nsslapd-changelogcompactdb-interval parameter has been removed from DS Starting with RHEL 9.0, the Directory Server changelog was integrated into the main database. As a result, the nsslapd-changelogcompactdb-interval parameter no longer exists.
2025-03-31Connections is the newest CD from the legendary keyboardist Bruce Katz and his dynamic band. Recorded at famed Capricorn Studios in Macon, Georgia, this album includes ten new original tunes that explore the connections between Bruce’s many influences: Blues, New Orleans R&B, Jam Blues, Soul-Jazz, and Blues Rock. Bruce was a longtime member of Gregg Allman’s Band and member of other Allman Brother “family bands”, including Butch Trucks’ Les Brers and Jaimoe’s Jasssz Band. Recording the album at Capricorn, the studio that gave the world the Allman Brothers and so many other greats, was an inspired choice for creating Connections, and the results are stunning! New members Aaron Lieberman (guitar, vocals) and Liviu Pop (drums) have revitalized the sound of the Bruce Katz Band. Founding member of God Street Wine, Aaron Lieberman, has added his expressive and soulful singing along with his brilliant guitar work. Liviu Pop on drums adds imagination and energy to the band and plays grooves that only he could create. Bruce plays Hammond B3, piano and Hammond organ bass on eight of the eleven tunes. Shaun Oakley, the grandson of original Allman Brothers bassist Berry Oakley, plays bass on three of the tunes.Bruce’s writing has never been better and the blending of his influences and Connections into his unique style of blues/roots/jam/soul-jazz music is fresh and exciting. Aaron contributes two of his own tunes on this album as well. As a critic once observed,” Bruce Katz’s music makes your mind think and gets your body moving too.” This new album will certainly do that! Connections reaches new heights in Bruce Katz’s long and storied career, creating music that has deep roots and is simultaneously new and original. The award- winning master of the Keyboard is back!
2025-03-29