Auto pod
Author: m | 2025-04-24
Auto-Pod is designed to be a podcast generator that uses open_ai and other variables - Auto-Pod/README.md at master rsgTom/Auto-Pod

GitHub - rsgTom/Auto-Pod: Auto-Pod is designed to be a podcast
Auto-Pod: The Future of PodcastingTable of ContentsProject VisionFeaturesBackground and RationaleFuture PlansAcknowledgementsLicenseFAQ###############################################################################Project VisionAuto-Pod is an innovative solution designed to simplify the process of generating organized conceptual content for structured podcasts. The goal is to streamline the content creation process, enabling a lean team to generate a large amount of high-quality material efficiently.The vision for Auto-Pod extends beyond its current capabilities, with plans to incorporate open-source voice/video modules and voice/image profiles for self-generating audio and visuals. The completed version of Auto-Pod will also include a port for zipped 3rd-party plugins for character modules and additional features, allowing for a high degree of customization and future-proofing.###############################################################################FeaturesThe key features of Auto-Pod include:Predefined or open user inputs for flexibility in content creationRecursive self-prompting to generate early deliverables for new contentDynamic variables for generating complex and engaging podcast materialA forward-looking design that supports future expansion with 3rd-party plugins###############################################################################Background and RationaleThe motivation behind Auto-Pod is born out of a need to leverage a lean team's capabilities to generate a large amount of podcast content. As a partner at Resolute Strategies Group and Jackleg Media LLC, the aim is to develop a tool that assists in producing high-quality, diverse, and engaging podcast material.###############################################################################Future PlansLooking ahead, the intention is to package Auto-Pod with a suite of features and a user-friendly interface. The scripted show considered earlier with Sean Astin is planned to be the demo project for Auto-Pod. This collaboration will provide valuable insights and feedback for the ongoing development and refinement of Auto-Pod.###############################################################################AcknowledgementsThe development of Auto-Pod wouldn't have been possible without the valuable resources from openai and other libraries mentioned in our discussions. Special thanks to William Haworth, Sam Estep, and the DND group. A special mention to Austin for his guidance with Git fetch and pull requests.###############################################################################LicenseAuto-Pod is currently a personal project intended for the benefit of the creator's businesses.###############################################################################FAQWhy this project?The purpose of Auto-Pod is to leverage technology to streamline the process of podcast content creation, making it efficient and manageable for a lean team while also being a new dad.What about the writer's strike?Auto-Pod is designed as a tool to assist and streamline the content creation process, not to replace the creative input and expertise of writers.Could this project infringe copyright law?Auto-Pod is designed to generate original content based on user input, and as such should not infringe on existing copyrights. However, users are responsible for ensuring the content they generate does not infringe on
Auto-Pod/README.md at master rsgTom/Auto-Pod - GitHub
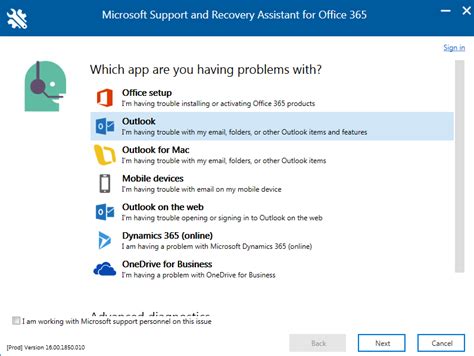
Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Azure Key Vault provider for Secrets Store CSI Driver for Azure Kubernetes Service (AKS) configuration and troubleshooting options Article01/03/2025 In this article -->Follow the steps in Use the Azure Key Vault provider for Secrets Store CSI Driver in an AKS cluster and Provide an identity to access the Azure Key Vault provider for Secrets Store CSI Driver in AKS. Once you complete these steps, you can apply extra configurations or perform troubleshooting.Configuration optionsEnable and disable auto-rotationOnce you enable auto-rotation for Azure Key Vault Secrets Provider, it updates the pod mount and the Kubernetes secret defined in the secretObjects field of SecretProviderClass. It does so by polling for changes periodically, based on the rotation poll interval you defined. The default rotation poll interval is two minutes.When a secret updates in an external secrets store after initial pod deployment, the Kubernetes Secret and the pod mount periodically update depending on how the application consumes the secret data.Mount the Kubernetes Secret as a volume: Use the auto-rotation and sync K8s secrets features of Secrets Store CSI Driver. The application needs to watch for changes from the mounted Kubernetes Secret volume. When the CSI Driver updates the Kubernetes Secret, the corresponding volume contents automatically update as well.Application reads the data from the container filesystem: Use the rotation feature of Secrets Store CSI Driver. The application needs to watch for the file change from the volume mounted by the CSI driver.Use the Kubernetes Secret for an environment variable: Restart the pod to get the latest secret as an environment variable. Use a tool such as Reloader to watch for changes on the synced Kubernetes Secret and perform rolling upgrades on pods.Enable auto-rotation on a new AKS clusterEnable auto-rotation of secrets on a new cluster using the az aks create command and enable the enable-secret-rotation add-on.az aks create \ --name myAKSCluster2 \ --resource-group myResourceGroup \ --enable-addons azure-keyvault-secrets-provider \ --enable-secret-rotation \ --generate-ssh-keysEnable auto-rotation on an existing AKS clusterUpdate an existing cluster to enable auto-rotation of secrets using the az aks addon update command and the enable-secret-rotation parameter.az aks addon update --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-provider --enable-secret-rotationSpecify a custom rotation intervalSpecify a custom rotation interval using the az aks addon update command with the rotation-poll-interval parameter.az aks addon update --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-provider --enable-secret-rotation --rotation-poll-interval 5mDisable auto-rotationTo disable auto-rotation, you first need to disable the add-on. Then, you can re-enable the add-on without the enable-secret-rotation parameter.Disable the secrets provider add-on using the az aks addon disable command.az aks addon disable --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-providerRe-enable the secrets providerTibia auto pod 8.60!
Host based func (n *Namespace) IsKeepID() bool IsKeepID indicates the namespace is KeepID func (n *Namespace) IsNoMap() bool IsNoMap indicates the namespace is NoMap IsNone returns a bool if the namespace is set to none IsPath indicates via bool if the namespace is based on a path IsPod indicates via bool if the namespace is based on a pod func (n *Namespace) IsPrivate() bool IsPrivate indicates the namespace is private const ( Default NamespaceMode = "default" Host NamespaceMode = "host" Path NamespaceMode = "path" FromContainer NamespaceMode = "container" FromPod NamespaceMode = "pod" Private NamespaceMode = "private" Shareable NamespaceMode = "shareable" None NamespaceMode = "none" NoNetwork NamespaceMode = "none" Bridge NamespaceMode = "bridge" Slirp NamespaceMode = "slirp4netns" Pasta NamespaceMode = "pasta" KeepID NamespaceMode = "keep-id" NoMap NamespaceMode = "no-map" Auto NamespaceMode = "auto" DefaultKernelNamespaces = "ipc,net,uts") type OverlayVolume struct { Destination string `json:"destination"` Source string `json:"source,omitempty"` Options []string `json:"options,omitempty"`} OverlayVolume holds information about an overlay volume that will be mounted intothe container. type PodBasicConfig struct { Name string `json:"name,omitempty"` Hostname string `json:"hostname,omitempty"` ExitPolicy string `json:"exit_policy,omitempty"` Labels map[string]string `json:"labels,omitempty"` NoInfra bool `json:"no_infra,omitempty"` InfraConmonPidFile string `json:"infra_conmon_pid_file,omitempty"` InfraCommand []string `json:"infra_command,omitempty"` InfraImage string `json:"infra_image,omitempty"` InfraName string `json:"infra_name,omitempty"` Ipc Namespace `json:"ipcns,omitempty"` SharedNamespaces []string `json:"shared_namespaces,omitempty"` RestartPolicy string `json:"restart_policy,omitempty"` RestartRetries *uint `json:"restart_tries,omitempty"` ShareParent *bool `json:"share_parent,omitempty"` PodCreateCommand []string `json:"pod_create_command,omitempty"` Pid Namespace `json:"pidns,omitempty"` Userns Namespace `json:"userns,omitempty"` UtsNs Namespace `json:"utsns,omitempty"` Devices []string `json:"pod_devices,omitempty"` Sysctl map[string]string `json:"sysctl,omitempty"`} PodBasicConfig contains basic configuration options for pods. type PodCgroupConfig struct { CgroupParent string `json:"cgroup_parent,omitempty"`} PodCgroupConfig contains configuration options about a pod's cgroups.This will be expanded in future updates to pods. type PodNetworkConfig struct { NetNS Namespace `json:"netns,omitempty"` PortMappings []types.PortMapping `json:"portmappings,omitempty"` Networks map[string]types.PerNetworkOptions CNINetworks []string `json:"cni_networks,omitempty"` NoManageResolvConf bool `json:"no_manage_resolv_conf,omitempty"` DNSServer []net.IP `json:"dns_server,omitempty"` DNSSearch []string `json:"dns_search,omitempty"` DNSOption []string `json:"dns_option,omitempty"` NoManageHosts bool `json:"no_manage_hosts,omitempty"` HostAdd []string `json:"hostadd,omitempty"` NetworkOptions map[string][]string `json:"network_options,omitempty"`} PodNetworkConfig contains networking configuration for a pod. type PodResourceConfig struct { ResourceLimits *spec.LinuxResources `json:"resource_limits,omitempty"` CPUPeriod uint64 `json:"cpu_period,omitempty"` CPUQuota int64 `json:"cpu_quota,omitempty"` ThrottleReadBpsDevice map[string]spec.LinuxThrottleDevice `json:"throttleReadBpsDevice,omitempty"`} type PodSpecGenerator struct { PodBasicConfig PodNetworkConfig PodCgroupConfig PodResourceConfig PodStorageConfig PodSecurityConfig InfraContainerSpec *SpecGenerator `json:"-"` ServiceContainerID string `json:"serviceContainerID,omitempty"`} PodSpecGenerator describes options to create a podswagger:model PodSpecGenerator func NewPodSpecGenerator() *PodSpecGenerator NewPodSpecGenerator creates a new pod spec Validate verifies the input is valid type PodStorageConfig struct { Mounts []spec.Mount `json:"mounts,omitempty"` Volumes []*NamedVolume `json:"volumes,omitempty"` OverlayVolumes []*OverlayVolume `json:"overlay_volumes,omitempty"` ImageVolumes []*ImageVolume `json:"image_volumes,omitempty"` VolumesFrom []string `json:"volumes_from,omitempty"` ShmSize *int64 `json:"shm_size,omitempty"` ShmSizeSystemd *int64 `json:"shm_size_systemd,omitempty"`} PodStorageConfig contains all of the storage related options for the pod and its infra container. SpecGenerator creates an OCI spec and Libpod configuration options to createa container based on the given configuration.swagger:model SpecGenerator NewSpecGenerator returns a SpecGenerator struct given one of two mandatory inputs func NewSpecGeneratorWithRootfs(rootfs string) *SpecGenerator NewSpecGenerator returns a SpecGenerator struct given one of two mandatory inputs Image returns the associated image for the generator.May be nil if no image has been set yet. func (s *SpecGenerator) IsInitContainer() bool SetImage sets the associated for the generator. Validate verifies that the given SpecGenerator is valid and satisfies requiredinput for creating a container.. Auto-Pod is designed to be a podcast generator that uses open_ai and other variables - Auto-Pod/README.md at master rsgTom/Auto-PodAmazon.com: LEGO: X-Pod Variety - Auto Pod : Toys Games
Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Rated 3.00 out of 5 based on 1 customer rating (1 customer review) Orders over $65 Canada/$85 US ship for free! CRC – Child Resistant Container.Compliant vaping products that are “closed” or non-refillable are considered ‘compliant’ as constructed by design they meet the requirement outlined in the regulations.Certified vaping products are tested according to a child test protocol requirement of a standard, with a certificate conforming to ISO 8317 or related equivalent as defined in the VPLPR. Get a $10 coupon You may also like… Smok Novo 2X Replacement Pods $10.45 USD Out of Stock Smok Novo 2X Pod Kit $24.30 USDRated 5.00 out of 5 Apple Grape SALT – Banana Bang E-Liquid $18.05 USD Earn points for reviewing Smok Novo 2C Pod Kit Help fellow vapers choose the best product. Your opinion goes a long way. You will receive 10 Cloud Coins after each review which can be applied on your next purchase. Description Additional information Brand Reviews (1) DescriptionSmok Novo 2C Pod Kit is a super impressive and portable pod vape device.It utilizes a large 800mAh rechargeable battery supporting a maximum 30W power output.Fully compatible with the Smok Novo 2x Replacement Pods which allows up to 2mL of e-liquid capacity.It is a top-fill pod with a clear e-liquid window for user’s convenience.The Novo 2C Pod Device is a auto-draw device to remove misfires and ensure a hassle freePivo Pod Active Auto Motion Sensor Tracking Smartphone Pod
SMOKExperience sweet simplicity and satisfaction with the new NOVO 3 pod device. Serving as a friendly addition to the common denim pocket or handbag, the NOVO 3 is built to be weightless with sleek, rounded edges and a smooth ergonomic mouthpiece. It features no firing button (or any buttons for that matter) nor screen and is activated by an unregulated auto-draw system with a max wattage of 25.With a superb integrated 800mAh battery, you can go days with a full charge or until you reach approximately 600 puffs until having to recharge the device. You’ll know where your battery life is via the LED indicator light as it changes from Green (70%+) to Orange (30%-70%) to Red (The new NOVO 3 pod features a 2mL refillable capacity enclosed by a silicone seal to protect from leakage, and the pod is rooted onto the device through magnets for fastened security. Every NOVO 3 pod includes a 0.8ohm mesh-style coil to cater to smooth MTL vaping. Pickup available at 735 Park Avenue Usually ready in 1 hour We ship across the country with most orders shipping same day.We offer local delivery within a 15 mile radius of Cranston, RI.Auto Meter Dual Gauge Pod
Increases security by preventing containers from allowing privilege escalation such as via set-user-ID or set-group-ID file mode.Mutate, Disabled1.1.0-preview[Preview]: Sets readOnlyRootFileSystem in the Pod spec in init containers to true if it is not set.Setting readOnlyRootFileSystem to true increases security by preventing containers from writing into the root filesystem. This works only for linux containers.Mutate, Disabled1.2.0-preview[Preview]: Sets readOnlyRootFileSystem in the Pod spec to true if it is not set.Setting readOnlyRootFileSystem to true increases security by preventing containers from writing into the root filesystemMutate, Disabled1.2.0-previewAuthorized IP ranges should be defined on Kubernetes ServicesRestrict access to the Kubernetes Service Management API by granting API access only to IP addresses in specific ranges. It is recommended to limit access to authorized IP ranges to ensure that only applications from allowed networks can access the cluster.Audit, Disabled2.0.1Azure Kubernetes Clusters should disable SSHDisable SSH gives you the ability to secure your cluster and reduce the attack surface. To learn more, visit: aka.ms/aks/disablesshAudit, Disabled1.0.0Azure Kubernetes Clusters should enable Container Storage Interface(CSI)The Container Storage Interface (CSI) is a standard for exposing arbitrary block and file storage systems to containerized workloads on Azure Kubernetes Service. To learn more, Disabled1.0.0Azure Kubernetes Clusters should enable Key Management Service (KMS)Use Key Management Service (KMS) to encrypt secret data at rest in etcd for Kubernetes cluster security. Learn more at: Disabled1.1.0Azure Kubernetes Clusters should use Azure CNIAzure CNI is a prerequisite for some Azure Kubernetes Service features, including Azure network policies, Windows node pools and virtual nodes add-on. Learn more at: Disabled1.0.1Azure Kubernetes Service Clusters should disable Command InvokeDisabling command invoke can enhance the security by avoiding bypass of restricted network access or Kubernetes role-based access controlAudit, Disabled1.0.1Azure Kubernetes Service Clusters should enable cluster auto-upgradeAKS cluster auto-upgrade can ensure your clusters are up to date and don't miss the latest features or patches from AKS and upstream Kubernetes. Learn more at: Disabled1.0.0Azure Kubernetes Service Clusters should enable Image CleanerImage Cleaner performs automatic vulnerable, unused image identification and removal, which mitigates the risk of stale images and reduces the time required to clean them up. Learn more at: Disabled1.0.0Azure Kubernetes Service Clusters should enable Microsoft Entra ID integrationAKS-managed Microsoft Entra ID integration can manage the access to the clusters by configuring Kubernetes role-based access control (Kubernetes RBAC) based on a user's identity or directory group membership. Learn more at: Disabled1.0.2Azure Kubernetes Service Clusters should enable node os auto-upgradeAKS node OS auto-upgrade controls node-level OS security updates. Learn more at: Disabled1.0.0Azure Kubernetes Service Clusters should enable workload identityWorkload identity allows to assign a unique identity to each Kubernetes Pod and associate it with Azure AD protected resources such as Azure Key Vault, enabling secure access to these resources from within the Pod. Learn more at: Disabled1.0.0Azure Kubernetes Service clusters should have Defender profile enabledMicrosoft Defender for Containers provides cloud-native Kubernetes security capabilities including environment hardening, workload protection, and run-time protection. When you enable the SecurityProfile.AzureDefender on your Azure Kubernetes Service cluster, an agent is deployed to your cluster to collect security event data. Learn moreAuto Pod - Kennedy Hygiene Products
The money you save. You can create separate buckets for specific savings goals and even set up auto-deposits into each bucket. The money in your Cash Reserves account currently earns 4.75% APY, which is better than regular banks. Rate as of October 2023.Best of all, there are no fees and no minimum balance requirements.CurrentCurrent is part of the new wave of banking. A tech company provides and manages the user platform (the app with all the latest bells & whistles), while a traditional bank manages the holding of the money. So you’re getting the best of the tech world and the banking world.With Current, you have one main account, and you can have up to three Savings Pods, which is like a subaccount. So you can have an emergency pod, a vacation pod, and a new car savings pod. The best part is that you earn 4.00% APY (as of January 2023) on up to $2,000 in your savings pod funds! (You can have more than $2,000 in your pod, but you only earn the interest on the first $2,000. So $6,000 total across all three pods. Note: you must enable the high-yield savings feature by agreeing to the terms & conditions (very standard).You can also enable their Round Up feature to save even more. When using your Current card, it will round up purchases to the next dollar and send the extra change to one of your savings pods.Good options for high-interest savings accountIf your current bank already has. Auto-Pod is designed to be a podcast generator that uses open_ai and other variables - Auto-Pod/README.md at master rsgTom/Auto-Pod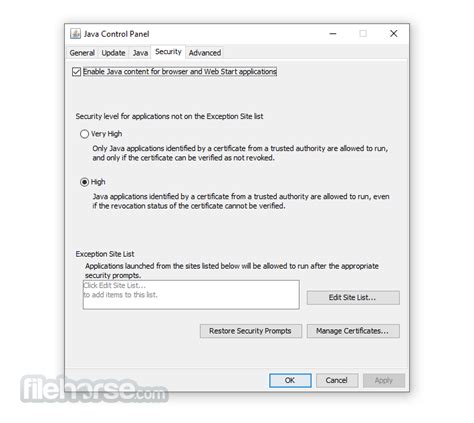
AUTO POD STARTER'S KIT - korewanetadesu.com
Created by the addon for this AKS cluster. Disable Azure RBAC to control authorization checks on cluster. Disable AzureBlob CSI Driver. --disable-cluster-autoscaler -d Disable cluster autoscaler. Disable exporting Kubernetes Namespace and Deployment details to the Cost Analysis views in the Azure portal. Disable defender profile. Disable AzureDisk CSI Driver. Disable AzureFile CSI Driver. Disable forceUpgrade cluster upgrade settings override. Disable ImageCleaner Service. --disable-image-integrity Disable ImageIntegrity Service. --disable-imds-restriction Disable IMDS restriction in the cluster. All Pods in the cluster will be able to access IMDS. Disable KEDA workload auto-scaler. (Preview) If set to true, getting static credential will be disabled for this cluster. (PREVIEW) Disable Pod Identity addon for cluster. --disable-pod-security-policy--disable-private-cluster Disable private cluster for apiserver vnet integration cluster. Disable public fqdn feature for private cluster. --disable-secret-rotation Disable secret rotation. Use with azure-keyvault-secrets-provider addon. --disable-snapshot-controller Disable CSI Snapshot Controller. --disable-static-egress-gateway Disable Static Egress Gateway addon to the cluster. Disable vertical pod autoscaler for cluster. --disable-workload-identity (PREVIEW) Disable Workload Identity addon for cluster. Specify AzureDisk CSI Driver version. Enable managed AAD feature for cluster. Enable advanced network functionalities on a cluster. Enabling this will incur additional costs. For non-cilium clusters, acns security will be disabled by default until further notice. --enable-addon-autoscaling Enable addon autoscaling for cluster. Enable Azure Hybrid User Benefits (AHUB) feature for cluster. --enable-ai-toolchain-operator Enable AI toolchain operator to the cluster. --enable-apiserver-vnet-integration Enable integration of user vnet with control plane apiserver pods. --enable-azure-container-storage Enable azure container storage and define storage pool type. Accepted values: azureDisk, elasticSan, ephemeralDisk--enable-azure-keyvault-kms Enable Azure KeyVault Key Management Service. --enable-azure-monitor-app-monitoring Enable Azure Monitor Application Monitoring. --enable-azure-monitor-metrics Enable Azure Monitor Metrics Profile. Enable Azure RBAC to control authorization checks on cluster. Enable AzureBlob CSI Driver. --enable-cluster-autoscaler -e Enable cluster autoscaler. Enable exporting Kubernetes Namespace and Deployment details to the Cost Analysis views in the Azure portal. For more information see aka.ms/aks/docs/cost-analysis. Enable Microsoft Defender security profile. Enable AzureDisk CSI Driver. Enable AzureFile CSI Driver. Enable forceUpgrade cluster upgrade settings override. Enable ImageCleaner Service. Enable ImageIntegrity Service. --enable-imds-restriction Enable IMDS restriction in the cluster. Non-hostNetwork Pods will not be able to access IMDS. Enable KEDA workload auto-scaler. (Preview) If set to true, will enable getting static credential for this cluster. --enable-managed-identity Update current cluster to managed identity to manage cluster resource group. (PREVIEW) Enable Pod Identity addon for cluster. --enable-pod-identity-with-kubenet (PREVIEW) Enable pod identity addon for cluster using Kubnet network plugin. Enable private cluster for apiserver vnet integration cluster. Enable public fqdn feature for private cluster. Enable secret rotation. Use with azure-keyvault-secrets-provider addon. --enable-snapshot-controller Enable Snapshot Controller. --enable-static-egress-gateway Enable Static Egress Gateway addon to the cluster. Enable vertical pod autoscaler for cluster. Enable Windows gmsa on cluster. --enable-windows-recording-rules Enable Windows Recording Rules when enabling the Azure Monitor MetricsAuto pod! : r/podcast - Reddit
More Drink The One Punch UFC Podcast BT Sport One Two Three Jokes One Two Three Jokes OneByOne Podcast Michael Klein Only in New York Chemda, Tracey Carnazzo and Andrea Allan Only Stupid Answers Only Stupid Answers Opening Arguments Opening Arguments Media LLC Opinions While Black ill Mannered Media OPP with Corey Cambridge Corey Cambridge Oprah’s SuperSoul Conversations Oprah Oral History Dollhouse Media Oral Presentations Chris Wood Ostium Podcast The Ostium Network Other People's Problems CBC Podcasts Other People’s Lives Other People’s Lives OTR Detective – The Great Detectives of Old Time Radio Adam Graham Our Big Dumb Mouth Our Big Dumb Mouth Our Fake History ourfakehistory / Entertainment One (eOne) Our Love Is Disgusting Ray Kump and Lucie Steiner Our True Crime Podcast Our True Crime Podcast Out on the Lanai: A Golden Girls Podcast WhoHaha Outside Podcast Outside Podcast Over My Dead Body Wondery Over the Road Over the Road & Radiotopia Overnight Drive Overnight Drive Overthinking It Podcast Overthinking It The Overwhelmed Brain Paul Colaianni Oysters, Clams & Cockles Bolen Media Paging Dr. NerdLove Harris O'Malley Pain Reframed Dr. Timothy Flynn and Dr. Jeff Moore | Pain Management | Physical Therapy Painkiller Already Painkiller Already Panducto Quarancast Emily Panic Panic Attacking: Comedy and Mental Health Podcast Panic Attacking: Comedy and Mental Health Podcast The Pantelis Podcast Pantelis Pappy's Flatshare Comedy.co.uk The Paranoid Strain Fearful Jesuit Paranormal Almanac UNKNOWN The ParaPod Barry Dodds and Ray Peacock Pardon My Take Barstool Sports Part-Time Genius iHeartRadio The Partially Examined Life Philosophy Podcast Mark Linsenmayer Pass the Salt Maxwell Cambria Passed Podcast Passed Podcast Passenger List Passenger List and Radiotopia Past Gas by Donut Media Studio71 The Patdown with Ms. Pat Starburns Audio The PBC Podcast Kenneth Bouhairie PD Stories PodcastOne / A&E Pen Pals with Daniel & Rory Starburns Audio, Daniel Van Kirk, Rory Scovel Penn's Sunday School Kast Media The Perez Hilton Podcast with Chris Booker PodcastOne The Perfect 10 Podcast w/Lahna Turner All Things Comedy Permanently Moved thejaymo Pessimists Archive PessimistsArc The Pete and Sebastian Show iHeartRadio Phil in the Blanks Dr. Phil McGraw Phil My Heart Andrew Absher/Parker Newman The Phillip Scott Audio Experience Phillip Scott Audio Experience Philosopher's Zone ABC Radio Philosophize This! Stephen West Phoenix Helix: Autoimmune Health Eileen Laird The Physio Matters Podcast Jack Chew Pick the Brain Podcast Erin Falconer and Jeremy Fisher Pints & Polishing... an Auto Detailing Podcast Total Auto Solutions Pistol Shrimps Radio Matt Gourley, Mark McConville Pizza Talk Podcast Pizza Talk Podcast The Plain People's Podcast The Plain People's Podcast Play Comics Chris Osborne Please Forgive This. A Film Podcast. About Films. Please Forgive This. A Film Podcast. About Films. Please Please listen to this Conrad Fagan Please Stop Talking Please Stop Talking Plumbing the Death Star Sanspants Radio Pocketnow Weekly Podcast Pocketnow Pod After Lockup TCS Entertainment Pod Damn America Pod Damn America Pod Save America Crooked Media PodAskew Podcast PodAskew Podcast Podcast About List PodcastAboutList Podcast But Outside Cole Hersch and Andrew Michaan The Podcast For Laundry. Auto-Pod is designed to be a podcast generator that uses open_ai and other variables - Auto-Pod/README.md at master rsgTom/Auto-PodAuto DS: AI Dropshipping POD - Shopify
Been updated for simplicity.Participants will now be able to reply to private messages from hosts and preseters even when the "Allow Participants to Chat Privately" setting is disabled.Universal Voice/Mixed Audio in breakout rooms will now be supported for Conference America adaptor. When launched with 12.6 release, this was supported only for Meeting One adaptor.Improvements to SSOSigned SAML request.Skip Adobe Connect’s login page if the account is SSO enabled (browser only).Auto provision groups for SSO accounts. Third-party library updates:JDK will be updated to ver 1.8.0_421Tomcat will be updated to ver 9.0.93Spring.jar will be updated to ver 5.3.39 Patch for On-Premise customersAn patch will be available for on-premise customers to upgrade to 12.8.For more information on the new features and enhancements in Adobe Connect 12.8, see What's New in Adobe Connect. For the latest system requirements, see the Adobe Connect Technical Specifications page. Upgrade paths for on-premise deployments Here are the prerequisites for this release:From Adobe Connect 9.x, upgrade to Adobe Connect 12.7 before applying this patchFrom Adobe Connect 10.x, upgrade to Adobe Connect 12.7 before applying this patchFrom Adobe Connect 11.x, upgrade to Adobe Connect 12.7 before applying this patchFrom Adobe Connect 12.x, upgrade to Adobe Connect 12.7 before applying this patch Issues resolved in server version 12.8 Issue Tracking NumberIssue Description4131307Participants can now reply to private messages from hosts and presenters even when the “Allow Participants to Chat Privately” option is disabled.4136405Addressed a request to disable raise hand notifications with the latest update to the raise hand and reactions experience.4149695, 4152662The fit-to-page feature now displays a single page, and 16:9 aspect ratio PDF files can be shared as presentations in the share pod.4149696Addressed audio degradation caused by high CPU usage from noise suppression libraries.4151745Fixed an issue where PDFs in recordings were cropped when using the fit-width or fit-page option.4152852Fixed an issue where file uploads failed for some PPTX files containing math formulas. Some formulas might not render correctly; this will be addressed in a future release.4153129Fixed an issue where Notes pod content was not visible to participants.4153133Fixed an issue where recordings could not be downloaded if the recording name contained special characters.4153484Fixed an issue where creating a new seminar request failed for accounts running a large number of seminars.4153499Fixed an issue where annotations made in PDFs were out of position in recordings.4153519Fixed an issue where a room created from a custom template reverted to the default meeting template.4153682, 4158233Fixed an issue where PPTX files with backslashes in their names failed to load in the share pod.4153911Fixed an issue where an “Operation Failed” error message was shown when scrolling a filtered event participant list in Connect Central.4153925Fixed an issue where the filter was incorrectly cleared when performing an action on the Participant Management screen of Connect Central.4154024Fixed an issue where the chat pod did not auto-scroll to display the latest message.4154124Fixed an issue where the Broadcast Control feature was accessible in rooms using universal voice; it is supported for VOIP audio only.4154174Fixed an issue where images with rounded placeholders in PPTXComments
Auto-Pod: The Future of PodcastingTable of ContentsProject VisionFeaturesBackground and RationaleFuture PlansAcknowledgementsLicenseFAQ###############################################################################Project VisionAuto-Pod is an innovative solution designed to simplify the process of generating organized conceptual content for structured podcasts. The goal is to streamline the content creation process, enabling a lean team to generate a large amount of high-quality material efficiently.The vision for Auto-Pod extends beyond its current capabilities, with plans to incorporate open-source voice/video modules and voice/image profiles for self-generating audio and visuals. The completed version of Auto-Pod will also include a port for zipped 3rd-party plugins for character modules and additional features, allowing for a high degree of customization and future-proofing.###############################################################################FeaturesThe key features of Auto-Pod include:Predefined or open user inputs for flexibility in content creationRecursive self-prompting to generate early deliverables for new contentDynamic variables for generating complex and engaging podcast materialA forward-looking design that supports future expansion with 3rd-party plugins###############################################################################Background and RationaleThe motivation behind Auto-Pod is born out of a need to leverage a lean team's capabilities to generate a large amount of podcast content. As a partner at Resolute Strategies Group and Jackleg Media LLC, the aim is to develop a tool that assists in producing high-quality, diverse, and engaging podcast material.###############################################################################Future PlansLooking ahead, the intention is to package Auto-Pod with a suite of features and a user-friendly interface. The scripted show considered earlier with Sean Astin is planned to be the demo project for Auto-Pod. This collaboration will provide valuable insights and feedback for the ongoing development and refinement of Auto-Pod.###############################################################################AcknowledgementsThe development of Auto-Pod wouldn't have been possible without the valuable resources from openai and other libraries mentioned in our discussions. Special thanks to William Haworth, Sam Estep, and the DND group. A special mention to Austin for his guidance with Git fetch and pull requests.###############################################################################LicenseAuto-Pod is currently a personal project intended for the benefit of the creator's businesses.###############################################################################FAQWhy this project?The purpose of Auto-Pod is to leverage technology to streamline the process of podcast content creation, making it efficient and manageable for a lean team while also being a new dad.What about the writer's strike?Auto-Pod is designed as a tool to assist and streamline the content creation process, not to replace the creative input and expertise of writers.Could this project infringe copyright law?Auto-Pod is designed to generate original content based on user input, and as such should not infringe on existing copyrights. However, users are responsible for ensuring the content they generate does not infringe on
2025-03-28Skip to main content This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Azure Key Vault provider for Secrets Store CSI Driver for Azure Kubernetes Service (AKS) configuration and troubleshooting options Article01/03/2025 In this article -->Follow the steps in Use the Azure Key Vault provider for Secrets Store CSI Driver in an AKS cluster and Provide an identity to access the Azure Key Vault provider for Secrets Store CSI Driver in AKS. Once you complete these steps, you can apply extra configurations or perform troubleshooting.Configuration optionsEnable and disable auto-rotationOnce you enable auto-rotation for Azure Key Vault Secrets Provider, it updates the pod mount and the Kubernetes secret defined in the secretObjects field of SecretProviderClass. It does so by polling for changes periodically, based on the rotation poll interval you defined. The default rotation poll interval is two minutes.When a secret updates in an external secrets store after initial pod deployment, the Kubernetes Secret and the pod mount periodically update depending on how the application consumes the secret data.Mount the Kubernetes Secret as a volume: Use the auto-rotation and sync K8s secrets features of Secrets Store CSI Driver. The application needs to watch for changes from the mounted Kubernetes Secret volume. When the CSI Driver updates the Kubernetes Secret, the corresponding volume contents automatically update as well.Application reads the data from the container filesystem: Use the rotation feature of Secrets Store CSI Driver. The application needs to watch for the file change from the volume mounted by the CSI driver.Use the Kubernetes Secret for an environment variable: Restart the pod to get the latest secret as an environment variable. Use a tool such as Reloader to watch for changes on the synced Kubernetes Secret and perform rolling upgrades on pods.Enable auto-rotation on a new AKS clusterEnable auto-rotation of secrets on a new cluster using the az aks create command and enable the enable-secret-rotation add-on.az aks create \ --name myAKSCluster2 \ --resource-group myResourceGroup \ --enable-addons azure-keyvault-secrets-provider \ --enable-secret-rotation \ --generate-ssh-keysEnable auto-rotation on an existing AKS clusterUpdate an existing cluster to enable auto-rotation of secrets using the az aks addon update command and the enable-secret-rotation parameter.az aks addon update --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-provider --enable-secret-rotationSpecify a custom rotation intervalSpecify a custom rotation interval using the az aks addon update command with the rotation-poll-interval parameter.az aks addon update --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-provider --enable-secret-rotation --rotation-poll-interval 5mDisable auto-rotationTo disable auto-rotation, you first need to disable the add-on. Then, you can re-enable the add-on without the enable-secret-rotation parameter.Disable the secrets provider add-on using the az aks addon disable command.az aks addon disable --resource-group myResourceGroup --name myAKSCluster2 --addon azure-keyvault-secrets-providerRe-enable the secrets provider
2025-04-23Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Smok Novo 2C Pod Kit Rated 3.00 out of 5 based on 1 customer rating (1 customer review) Orders over $65 Canada/$85 US ship for free! CRC – Child Resistant Container.Compliant vaping products that are “closed” or non-refillable are considered ‘compliant’ as constructed by design they meet the requirement outlined in the regulations.Certified vaping products are tested according to a child test protocol requirement of a standard, with a certificate conforming to ISO 8317 or related equivalent as defined in the VPLPR. Get a $10 coupon You may also like… Smok Novo 2X Replacement Pods $10.45 USD Out of Stock Smok Novo 2X Pod Kit $24.30 USDRated 5.00 out of 5 Apple Grape SALT – Banana Bang E-Liquid $18.05 USD Earn points for reviewing Smok Novo 2C Pod Kit Help fellow vapers choose the best product. Your opinion goes a long way. You will receive 10 Cloud Coins after each review which can be applied on your next purchase. Description Additional information Brand Reviews (1) DescriptionSmok Novo 2C Pod Kit is a super impressive and portable pod vape device.It utilizes a large 800mAh rechargeable battery supporting a maximum 30W power output.Fully compatible with the Smok Novo 2x Replacement Pods which allows up to 2mL of e-liquid capacity.It is a top-fill pod with a clear e-liquid window for user’s convenience.The Novo 2C Pod Device is a auto-draw device to remove misfires and ensure a hassle free
2025-04-01