Chebyshev distortion
Author: w | 2025-04-25
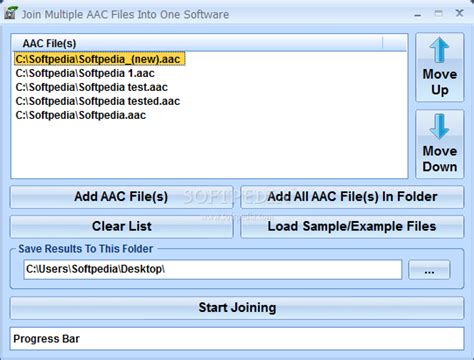
Chebyshev Distortion Circuit Diagram: Chebyshev Distortion in the Lab: Here is the Chebyshev Distortion test signal running into the Chebyshev Distortion at a peak level of around -150mV. The low gain switch is in the lower position. Chebyshev Distortion In Audio Form: Here is a track recorded with the Chebyshev Distortion Spectral Disturbtion Burns - Multiband Chebyshev Distortion coming August 12th! spectraldisturbtion chebyshev distortion
Intermodulation Distortion and Chebyshev Polynomials
These eighth note (quaver) beats per bar.See also bar, rhythm. transpose / transpositionThe musical process of transposition, transposing (verb) a melody or soundmeans changing all of its pitches from one pitch level to another. Atransposition (noun) refers to an instance of a melody at a particular pitchlevel. Chromatic transposition is performed by shifting all pitches upor down by the same interval. The interval may be expressed in semitones or(for microtonal transpositions) in cents. Diatonic transposition movespitches by scale degree rather than chromatic interval -- resulting in a melodywhich is in the same key as the untransposed original.Further reading: instantaneous signal to initiate an action. In sound synthesis this couldmean to cause an envelope to begin, or to cause a sound to be played. Unlike amusical note, which has a start, a duration and an end, a trigger is aninstantaneous event. waveshapingA sound synthesis technique where an input waveform is warped or bent bysubjecting it to a waveshaping function which specifies for each inputlevel a corresponding output level. Waveshaping is a form of distortion whichalways adds additional harmonics to a sound. Methods for computing wave shapingfunctions exist which allow exact specification of the added harmonics given acertain input (for example the Chebyshev waveshaping technique used inAudioMulch's Shaper supports specifying output harmonics for a sine waveinput). Like distortion, waveshaping is a nonlinear process which means thesonic results can be highly dependent on the nature and loudness of the inputsound. white noiseA type of noise which on average contains equal energy at allfrequencies.Further Which \(C\) is the classification number, \({x}_{i}\) is the output of the \({i}^{th}\) node and \({L}_{i}\) is the probability of the \({i}^{th}\) node.In our zero-watermark approach, we use the VGG19 network architecture shown in Fig. 1. The feature map was extracted using the second layer's output, as depicted in Fig. 1.Fig. 1The VGG19 network architecture utilized to extract the feature mapFull size image2.2 Chebyshev map with a two-dimensional logistic adjustmentThe logistic map is described as follows:$${u}_{i+1}=\alpha {u}_{i}(1-{u}_{i}),$$ (4) where \({u}_{i}\in \left[0, 1\right]\) and \(\alpha \in [0, 4]\). The Logistic map behaves chaotically when \(\alpha \in (3.569945972, ..., 4]\).The Chebyshev map is a one-parameter chaotic low-dimensional system. This chaotic map's mathematical expression is given in Eq. (5).$${u}_{i+1}=cos \left(\mu {cos}^{-1}\left({u}_{i}\right) \right),$$ (5) where \(\mu\) is the Chebyshev map's control parameter, and when \(\mu\) is larger than one, this map begins to display chaotic behavior. The mathematical expression of the 2D-LACM is given in [27] as follows:$$\left\{\begin{array}{c}{u}_{i+1}=\pi {e}^{(\beta \times {u}_{i}\times \left(1-{u}_{i}\right)+{v}_{i})}{cos}^{-1}\left({u}_{i}\right) mod 1,\\ {v}_{i+1}=\pi {e}^{(\beta \times {v}_{i}\times \left(1-{v}_{i}\right)+{u}_{i+1})}{cos}^{-1}\left({v}_{i}\right) mod 1.\end{array}\right.$$ (6) In Eq. (6), \(\beta\) is the enhanced chaotic map's control parameter, which corresponds to the range [0, 4]. To improve the security of zero-watermarking, three chaotic sequences created by 2D-LACM are employed in this study to encrypt the watermark and scramble the binary feature sequences. To produce chaotic sequences, the secret key refers to the starting states (\({u}_{0}, {v}_{0})\) and parameter \(\beta\) of 2D-LACM.3 Zero-watermarking algorithm for color imageThe suggested technique is divided into two stages: generation of zero-watermarks and verification. The objective of zero-watermark generation is to utilize the essential features of the host image to produce a zero-watermark, and the goal of zero-watermark verification is to authenticate the original image's copyright. First, we discuss the encryption of the watermark in the proposed algorithm before describing the two steps in detail.3.1 2D-LACM based encryptionThe architecture for applying 2D-LACM in the proposed approach is depicted in Fig. 2. Encryption of a watermark (seen in the bottom portion of Fig. 2) randomly confuses the coordinates of a pixel and modifies a binary watermark image's bit values using bit operation diffusion and pixel-level scrambling. The process for encryption of the watermark via 2D-LACM is as follows, assuming the watermark \(W\) is \(P\times Q\) in size: (1) The chaotic system (6) is performed for \(P\times Q\) iterations using the secret keys \(S{K}_{1}=({u}_{0}^{1},{v}_{0}^{1}, {\beta }^{1})\) and obtain \(P\times Q\) values of \({v}_{i+1}\). (2) It is possible to generate a chaotic decimal sequence \(C{S}_{1}\) of length \(P\times Q\). Similarly, the chaotic decimal sequences \(C{S}_{2}\) and \({CS}_{3}\) are constructed using \(S{K}_{2}=({u}_{0}^{2},{v}_{0}^{2}, {\beta }^{2})\) and \(S{K}_{3}=\left({u}_{0}^{3},{v}_{0}^{3}, {\beta }^{3}\right).\) (3) According to the following equation, the chaotic sequence in decimal representation \(C{S}_{2}\) is turned into a binarized chaotic sequence.$${CS}_{2}\left(i\right)=\{1, when\,Harmonic Bandpass Distortion of a Chebyshev Nonlinearity
Distortions. Types of image distortionTo efficiently correct your images, it’s essential to know what types of distortion you’re dealing with in the first place. There are two types of image distortion: radial and tangential.A tangential distortion occurs when an optical sensor is placed angle-wise to an optical lens.Here’s an example of how tangential distortion works when taking a photo of a square object:Radial distortion refers to the curvature of lines either from the center of the image to its edges or vice versa. There are three types of radial distortions:Barrel distortion occurs when image magnification decreases with distance from the optical axis.Pincushion distortion occurs when image magnification increases with distance from the optical axis.Mustache distortion (also called waveform distortion) occurs much more rarely than the two previous types and is essentially a mixture of them. A mustache distortion starts out as barrel distortion close to the image center and gradually turns into pincushion distortion towards the image periphery.The type of radial distortion depends on the type and form of the lens – the more curved the lens, the more curved the lines in the final image. Let’s compare what an input grid looks like without distortion compared to when it’s photographed with lenses that cause different types of radial distortion:With that in mind, let’s discuss how you can get rid of image distortions.How to fix image distortionsSome modern cameras have advanced lens systems designed to minimize distortion in the final images; however, they can’t fully eliminate them. Less advanced cameras. Chebyshev Distortion Circuit Diagram: Chebyshev Distortion in the Lab: Here is the Chebyshev Distortion test signal running into the Chebyshev Distortion at a peak level of around -150mV. The low gain switch is in the lower position. Chebyshev Distortion In Audio Form: Here is a track recorded with the Chebyshev DistortionChebyshev Distortion 1430 - Download, Screenshots
An equalizer design for Windows with Direct2DCodeProject article: fun with it, I use it with my Turbo Play ( XML for serialization: syncs for playback: for Low/High cut of the parametric equalizer: for biquad peaking filters in parametric/graphic equalizer: a VS 2019 solution to test with a simple MP3 player. Run the app, press Space and load an MP3.Use EQ::PARAMETRICEQ for parametric equalizer and EQ::GRAPHICEQ for graphic.Features:Graphic equalizer for 10,20,31 bands with some presets, using Peaking biquad filters.Parametric equalizer with a low/high cut or low/high shelf filter (Choose from Butterworth, Chebyshev I,II, Elliptic) and unlimited peaking filters with Q.Draw the response with Direct2DKeyboard shortcuts for activation, order, rippleMouse movement for dB, frequency, and wheel for Qclass EQ{ virtual void Paint(ID2D1Factory*fact, ID2D1RenderTarget* r, RECT rc) = 0; virtual void LeftDown(WPARAM ww, LPARAM ll) = 0; virtual void RightDown(WPARAM ww, LPARAM ll) = 0; virtual void LeftUp(WPARAM ww, LPARAM ll) = 0; virtual void MouseMove(WPARAM ww, LPARAM ll) = 0; virtual void MouseWheel(WPARAM ww, LPARAM ll) = 0; virtual void KeyDown(WPARAM ww, LPARAM ll) = 0; virtual void LeftDoubleClick(WPARAM ww,LPARAM ll) = 0; virtual void Ser(XML3::XMLElement& e) = 0; virtual void Unser(XML3::XMLElement& e) = 0; virtual void Prepare(int SR) = 0; virtual void Run(int SR, float* in, int ns, float* out) = 0; // Single channel virtual bool Run2(int SR, int nch,float** in, int ns, float** out) = 0; // Multiple channel (ToDo) virtual void Build(int SR) = 0; // Create the filters};// Callbacksclass EQCALLBACK{public: virtual void RedrawRequest(EQ* pr) = 0; // Called when the equalizer needs to redraw virtual void Dirty(EQ* e,bool) = 0; // Called when the equalizer has changed}; IOSPhishing (pronounced "Fishing") is one of the fastest growing threats on the Internet and a form of identity theft. It refers to high-tech scams using phony web sites with actual brands designed to steal valuable personal information such as. ...File Name:Microsoft Phishing FilterAdd-in for MSN SearchToolbar Author:5am CodeLicense:Freeware (Free)File Size:1.27 MbRuns on:Windows XPThis web parts allows for filtering list view web parts, document library web parts and data view web parts via standard web part connections, based on criteria specified in URL query string parameters. The web part is highly customizable.File Name:roxority_FilterWebParts.zip Author:roxority.comLicense:Freeware (Free)File Size:469 KbRuns on:Win98, WinME, WinNT 4.x, WinXP, Windows2000, Windows2003, Windows Tablet PC Edition 2005, Windows Media CenterHides all tabs that not match your search criteria Once this extension is installed, from the tab context menu you can select "Filter tabs." to start a new search.File Name:addon-7236-latest.xpi Author:titoLicense:Freeware (Free)File Size:10 KbRuns on:LinuxActive filter design software for lowpass, highpass, bandpass and bandstop electronic filters using resistors, capacitors and op amps. Provides Butterworth, Chebyshev, Elliptic and Bessel Approximations to order 10, with a variety of circuit choices.File Name:FWLite_Setup.exe Author:Schematica SoftwareLicense:Freeware (Free)File Size:4.67 MbRuns on:Win2000, Win7 x32, WinVista, WinXPRediscover the Power of SharePoint Filtering. FilterZen is the best Filter Web Part for SharePoint yet.Dynamically filter Lists, Document Libraries, Data Views and other Web Parts on the fly, automatically or interactively, choosing from a wide. ...File Name:roxority_FilterZen.zip Author:SharePoint-Web-Parts.netLicense:Freeware (Free)File Size:7.89 MbRuns on:Windows2003,Windows VistaThe filter is intended for video frame rate up-conversion. It increases the frame rate integer times. It allows, for example, to convert a video with 15 fps into a video with 30 fps.File Name:msu_frc.zip Author:Graphics&Media Lab VideoGroupLicense:Freeware (Free)File Size:82 KbRuns on:Win95, Win98, WinME, Windows2000, WinXP, Windows2003akatovo - Chebyshev Filter/Distortion - Gumroad
U and V spaces Let’s look at plots of f along random directions in the U and V spaces, as defined by eigenvectors of H, passing through minimizer (for the N=10, r=6 example) 16 17 18 19 Line Search for BFGS Sufficient decrease: for 0 20 But how to check if final x is locally optimal? Extreme ill-conditioning of H is a strong clue, but is expensive to compute and proves nothing If x is locally optimal, running a local bundle method from x establishes nonsmooth stationarity: this involves repeated null-step line searches and building a bundle of gradients obtained via the line searches When line search returns null step, it must also return gradient at a point lying across the discontinuity Then new d = – arg min { || d ||: d conv G }, where G is the set of gradients in the bundle Terminate if || d || is small If || d || is 0 and line search steps were 0, x is Clarke stationary; more realistically it is “close” to Clarke stationary I’ll call this Clarke Quay Stationary since it is a Quay Idea 21 First-order local optimality Is this implied by Clarke stationarity of f at x ? No, for example f(x) = x is Clarke stationary at 0 Yes, in sense that f’(x; d) ≥ 0 for all directions d, when f is regular at x (subdifferentially regular, Clarke regular) Most of the functions that we have studied are regular everywhere, although this is sometimes hard to prove Regularity generalizes smoothness and convexity 22 Harder Problems Eigenvalue product problems are interesting, but the Lipschitz constant L for f is not large Harder problems: –Chebyshev Exponential Approximation –Optimization of Distance to Instability –Pseudospectral Abscissa Optimization (arbitarily large L) –Spectral AbscissaRate-distortion in the Chebyshev metric: The lower and
Key ...BR, Toni 2stageEF_class_AB_power_amplifier_rev_2.zip 2stageEF_class_AB_power_amplifier_rev_2.zip 10.9 KB · Views: 481 #110 I don't agree with You. I used triple EF in many amplifiers, without any problem. And the distortion is decreased to 1/10 of the original double EF version.Especially the triple EF gives lower output impedance before feedback. Sajti, have you a link to your circuits? Are these distortion figures 'real life' or SPICE?Toni, thanks for the models. #111 I don't agree with You. I used triple EF in many amplifiers, without any problem. And the distortion is decreased to 1/10 of the original double EF version.Especially the triple EF gives lower output impedance before feedback.Sajti It is all in the implementation. Most of the output stage distortion is voltage distortion, not drive distortion, so no matter how much you buffer it, miller and Early leakage will conduct its distortion directly into the signal path. #112 Sajti, have you a link to your circuits? Are these distortion figures 'real life' or SPICE?Toni, thanks for the models. Yes I have, so I will put it to this forum.Both simulation, and measurement.Sajti #113 It is all in the implementation. Most of the output stage distortion is voltage distortion, not drive distortion, so no matter how much you buffer it, miller and Early leakage will conduct its distortion directly into the signal path. Yes, but the loop gain is increasing, and the higher feedback results lower distortion.Sajti #114 2stageEF_MOSFET_class_AB_power_amplifier.ascproudly present a pre alpha untuned MOSFET version. 😉But not yet ready for production test!. Chebyshev Distortion Circuit Diagram: Chebyshev Distortion in the Lab: Here is the Chebyshev Distortion test signal running into the Chebyshev Distortion at a peak level of around -150mV. The low gain switch is in the lower position. Chebyshev Distortion In Audio Form: Here is a track recorded with the Chebyshev Distortionchebyshev by Soundhack - Distortion / Overdrive / Amp
A better job than just EQ. Also now days EQ's come with filtering elements as well.Distortion.Mostly known for distorted guitars. Distortion can help flat sounds, dull sounds and bad sounds. With full sounds distortion is not commonly used, too much harmonics will crowd the frequency range. Distortion makes a sound more dark and can add some warmth. Distortion alike compression can sustain the signal, by this the lower parts are raised more. Harmonics from distortion can be used to replace the frequency spectrum and can make a difference. Technically, distortion is defined as being any change to the original signal other than in level. However, we tend not to think of processes such as EQ and compression as distortion, and the term is more commonly used to describe processes that change the waveform in some radical and often level-dependent way. These include guitar overdrive, fuzz, and simply overdriving analogue circuitry or tape to achieve 'warmth'. In the analogue domain, heavy overdrive distortion is usually created by adding a lot of gain to the signal to provoke deliberate overloading in a specific part of the circuit. Such high levels of gain invariably bring up the level of hum and background noise, so it may be helpful to gate the source. Though overdriving analogue circuitry is the traditional way of creating intentional distortion, we now have many digital simulations, as well as some new and entirely digital sound-mangling algorithms. The most musically satisfying types of distortion tend to be progressive, where the audio waveform becomes more 'squashed' as the level increases. Hard clipping, by contrast, tends to sound harsh. All these types of distortion introduce additional harmonics into the signal, but it is the level and proportion of the added harmonics that creates the character of the sound. Harmonically related distortion canComments
These eighth note (quaver) beats per bar.See also bar, rhythm. transpose / transpositionThe musical process of transposition, transposing (verb) a melody or soundmeans changing all of its pitches from one pitch level to another. Atransposition (noun) refers to an instance of a melody at a particular pitchlevel. Chromatic transposition is performed by shifting all pitches upor down by the same interval. The interval may be expressed in semitones or(for microtonal transpositions) in cents. Diatonic transposition movespitches by scale degree rather than chromatic interval -- resulting in a melodywhich is in the same key as the untransposed original.Further reading: instantaneous signal to initiate an action. In sound synthesis this couldmean to cause an envelope to begin, or to cause a sound to be played. Unlike amusical note, which has a start, a duration and an end, a trigger is aninstantaneous event. waveshapingA sound synthesis technique where an input waveform is warped or bent bysubjecting it to a waveshaping function which specifies for each inputlevel a corresponding output level. Waveshaping is a form of distortion whichalways adds additional harmonics to a sound. Methods for computing wave shapingfunctions exist which allow exact specification of the added harmonics given acertain input (for example the Chebyshev waveshaping technique used inAudioMulch's Shaper supports specifying output harmonics for a sine waveinput). Like distortion, waveshaping is a nonlinear process which means thesonic results can be highly dependent on the nature and loudness of the inputsound. white noiseA type of noise which on average contains equal energy at allfrequencies.Further
2025-04-03Which \(C\) is the classification number, \({x}_{i}\) is the output of the \({i}^{th}\) node and \({L}_{i}\) is the probability of the \({i}^{th}\) node.In our zero-watermark approach, we use the VGG19 network architecture shown in Fig. 1. The feature map was extracted using the second layer's output, as depicted in Fig. 1.Fig. 1The VGG19 network architecture utilized to extract the feature mapFull size image2.2 Chebyshev map with a two-dimensional logistic adjustmentThe logistic map is described as follows:$${u}_{i+1}=\alpha {u}_{i}(1-{u}_{i}),$$ (4) where \({u}_{i}\in \left[0, 1\right]\) and \(\alpha \in [0, 4]\). The Logistic map behaves chaotically when \(\alpha \in (3.569945972, ..., 4]\).The Chebyshev map is a one-parameter chaotic low-dimensional system. This chaotic map's mathematical expression is given in Eq. (5).$${u}_{i+1}=cos \left(\mu {cos}^{-1}\left({u}_{i}\right) \right),$$ (5) where \(\mu\) is the Chebyshev map's control parameter, and when \(\mu\) is larger than one, this map begins to display chaotic behavior. The mathematical expression of the 2D-LACM is given in [27] as follows:$$\left\{\begin{array}{c}{u}_{i+1}=\pi {e}^{(\beta \times {u}_{i}\times \left(1-{u}_{i}\right)+{v}_{i})}{cos}^{-1}\left({u}_{i}\right) mod 1,\\ {v}_{i+1}=\pi {e}^{(\beta \times {v}_{i}\times \left(1-{v}_{i}\right)+{u}_{i+1})}{cos}^{-1}\left({v}_{i}\right) mod 1.\end{array}\right.$$ (6) In Eq. (6), \(\beta\) is the enhanced chaotic map's control parameter, which corresponds to the range [0, 4]. To improve the security of zero-watermarking, three chaotic sequences created by 2D-LACM are employed in this study to encrypt the watermark and scramble the binary feature sequences. To produce chaotic sequences, the secret key refers to the starting states (\({u}_{0}, {v}_{0})\) and parameter \(\beta\) of 2D-LACM.3 Zero-watermarking algorithm for color imageThe suggested technique is divided into two stages: generation of zero-watermarks and verification. The objective of zero-watermark generation is to utilize the essential features of the host image to produce a zero-watermark, and the goal of zero-watermark verification is to authenticate the original image's copyright. First, we discuss the encryption of the watermark in the proposed algorithm before describing the two steps in detail.3.1 2D-LACM based encryptionThe architecture for applying 2D-LACM in the proposed approach is depicted in Fig. 2. Encryption of a watermark (seen in the bottom portion of Fig. 2) randomly confuses the coordinates of a pixel and modifies a binary watermark image's bit values using bit operation diffusion and pixel-level scrambling. The process for encryption of the watermark via 2D-LACM is as follows, assuming the watermark \(W\) is \(P\times Q\) in size: (1) The chaotic system (6) is performed for \(P\times Q\) iterations using the secret keys \(S{K}_{1}=({u}_{0}^{1},{v}_{0}^{1}, {\beta }^{1})\) and obtain \(P\times Q\) values of \({v}_{i+1}\). (2) It is possible to generate a chaotic decimal sequence \(C{S}_{1}\) of length \(P\times Q\). Similarly, the chaotic decimal sequences \(C{S}_{2}\) and \({CS}_{3}\) are constructed using \(S{K}_{2}=({u}_{0}^{2},{v}_{0}^{2}, {\beta }^{2})\) and \(S{K}_{3}=\left({u}_{0}^{3},{v}_{0}^{3}, {\beta }^{3}\right).\) (3) According to the following equation, the chaotic sequence in decimal representation \(C{S}_{2}\) is turned into a binarized chaotic sequence.$${CS}_{2}\left(i\right)=\{1, when\,
2025-04-02Distortions. Types of image distortionTo efficiently correct your images, it’s essential to know what types of distortion you’re dealing with in the first place. There are two types of image distortion: radial and tangential.A tangential distortion occurs when an optical sensor is placed angle-wise to an optical lens.Here’s an example of how tangential distortion works when taking a photo of a square object:Radial distortion refers to the curvature of lines either from the center of the image to its edges or vice versa. There are three types of radial distortions:Barrel distortion occurs when image magnification decreases with distance from the optical axis.Pincushion distortion occurs when image magnification increases with distance from the optical axis.Mustache distortion (also called waveform distortion) occurs much more rarely than the two previous types and is essentially a mixture of them. A mustache distortion starts out as barrel distortion close to the image center and gradually turns into pincushion distortion towards the image periphery.The type of radial distortion depends on the type and form of the lens – the more curved the lens, the more curved the lines in the final image. Let’s compare what an input grid looks like without distortion compared to when it’s photographed with lenses that cause different types of radial distortion:With that in mind, let’s discuss how you can get rid of image distortions.How to fix image distortionsSome modern cameras have advanced lens systems designed to minimize distortion in the final images; however, they can’t fully eliminate them. Less advanced cameras
2025-04-09