Rawcap
Author: r | 2025-04-24

download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewing download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewing

[RawCap ] System.Net.Sockets.SocketTaskExtensions
One. But you’re probably not aware that RawCap is our second most popular tool in terms of downloads, with around 100 unique downloads every day. RawCap started out as just being a quick hack that we released for free to the community in 2011 without expecting it to gain much attention. However, it quickly gained popularity, maybe due to the fact that it’s just a tiny .exe file and that it doesn’t require any external libraries or DLL’s to sniff network traffic (other than the .NET Framework). RawCap embraces the Unix philosophy to do only one thing, and do it well. Thanks to RawCap’s simplicity we have only needed to make a few minor updates of the tool since its first release 9 years ago. However, today we’re finally adding some new features that have been requested by users over the years. One such feature is that RawCap now automatically creates a Windows firewall rule when the tool is started. Before this feature was introduced users would have to run wf.msc (i.e. the "Windows Defender Firewall with Advanced Security") and manually create an inbound rule to allow RawCap.exe to receive incoming traffic. Without such a firewall rule RawCap would only be able to capture outgoing traffic. RawCap can be started in two different modes. Either as an interactive console application, or as a “normal” command line utility. Run RawCap.exe without any arguments, or simply double click the RawCap.exe icon to use the interactive mode. You will then be asked which
win-rawcap/README.md at master chengyuhui/win-rawcap
Interface to capture packets from and what filename you’d like to save them to. F:\Tools>RawCap.exe Network interfaces: 0. 192.168.0.17 Local Area Connection 1. 192.168.0.47 Wireless Network Connection 2. 90.130.211.54 3G UMTS Internet 3. 192.168.111.1 VMware Network Adapter VMnet1 4. 192.168.222.1 VMware Network Adapter VMnet2 5. 127.0.0.1 Loopback Pseudo-Interface Select network interface to sniff [default '0']: 1 Output path or filename [default 'dumpfile.pcap']: Sniffing IP : 192.168.0.47 Output File : dumpfile.pcap --- Press [Ctrl]+C to stop --- Packets : 1337 The other alternative is to supply all the arguments to RawCap when it is started. Use “RawCap --help” to show which arguments you can use. You’ll need to use this mode if you want to write the captured traffic to standard output (stdout) or a named pipe, or if you want RawCap to automatically stop capturing after a certain time or packet count. F:\Tools>RawCap.exe --help NETRESEC RawCap version 0.2.0.0 Usage: RawCap.exe [OPTIONS] can be an interface number or IP address can be filename, stdout (-) or named pipe (starting with \\.\pipe\) OPTIONS: -f Flush data to file after each packet (no buffer) -c Stop sniffing after receiving packets -s Stop sniffing after seconds -m Disable automatic creation of RawCap firewall entry -q Quiet, don't print packet count to standard out INTERFACES: 0. IP : 169.254.63.243 NIC Name : Local Area Connection NIC Type : Ethernet 1. IP : 192.168.1.129 NIC Name : WiFi NIC Type : Wireless80211 2. IP : 127.0.0.1 NIC Name : Loopback Pseudo-Interface 1 NIC Type : LoopbackRawCap - FREE Download RawCap 0.1.4.0 Misc Internet - WinSite
What is the default output format for the WinPmem tool? AFF4 file format (D) Signup and view all the answers Which function is performed by the Forensic Toolkit (FTK)? Scan slack space for file fragments (A) Signup and view all the answers What will happen when the 'Capture!' button is clicked in Ram Capturer? A memory image will be saved (B) Signup and view all the answers How does EnCase handle the acquisition of files or drives? Captures selected files or full drives (D) Signup and view all the answers Which of the following best describes the primary function of WinPmem? Memory acquisition from running systems (A) Signup and view all the answers What type of evidence can be collected from network devices like switches and routers? Access logs and configuration changes (D) Signup and view all the answers What is the primary purpose of the Argus monitor in the operations, performance, and security management package? To capture and combine packets into flow records (C) Signup and view all the answers Which of the following is NOT a feature of Wireshark? Command line interface only (D) Signup and view all the answers What is a major drawback of using WinPcap for network forensics? It needs to be installed on the system (C) Signup and view all the answers When using tcpdump, what is an important prerequisite for performing a packet capture? Having administrative privileges (A) Signup and view all the answers What is a unique feature of RawCap compared to other packet capturing tools? It can be run without installation on the system (D) Signup and view all the answers Why is packet capturing considered critical in network forensics? It provides insight into potential C2 IP address traffic (B) Signup and view all the answers Which of the following tools. download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewing download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewingHow to: Record in Rawcap
3. IP : 10.165.240.132 NIC Name : Mobile 12 NIC Type : Wwanpp Example 1: RawCap.exe 0 dumpfile.pcap Example 2: RawCap.exe -s 60 127.0.0.1 localhost.pcap Example 3: RawCap.exe 127.0.0.1 \\.\pipe\RawCap Example 4: RawCap.exe -q 127.0.0.1 - | Wireshark.exe -i - -k As you can see, running “RawCap.exe -s 60 127.0.0.1 localhost.pcap” will capture packets from localhost to a file called “localhost.pcap” for 60 seconds and then exit. There are a couple of drawbacks with the new RawCap version though, it is a larger binary (48kB instead of 23kB) and it uses more CPU and RAM compared to the old version. We will therefore continue making the old RawCap version available to anyone who might need it. Visit the RawCap product page to download this tool and learn more. Posted by Erik Hjelmvik on Thursday, 30 January 2020 14:32:00 (UTC/GMT) Tags: #Netresec #RawCap #sniffer #PCAP #named pipe #Wireshark #WiFi #loopback #127.0.0.1 Short URL: Erik Hjelmvik , Wednesday, 28 September 2016 11:45:00 (UTC/GMT) PacketCache lets you Go Back in Time Have you ever wanted to go back in time to get a PCAP of something strange that just happened on a PC? I sure have, many times, which is why we are now releasing a new tool called PacketCache. PacketCache maintains a hive of the most important and recent packets, so that they can be retrieved later on, if there is a need. Network forensics and incident response is performed post-event, but requires that packet have already been captured during the event[RawCap 에러] System.Net.Sockets.SocketTaskExtensions'
Port 57008. Go back to the Mikrotik router, where you start the sniffer with “/tool sniffer start” or by clicking the “Start” button in the WebFig. You should now see the Frames counter increasing in NetworkMiner's TZSP window. You’ll probably also notice that artifacts get added to the main NetworkMiner window in the background as more packets are received. Close the sniffer by running “/tool sniffer stop” or clicking the “Stop” button in WebFig, then click “Stop” in NetworkMiner. You can now close NetworkMiner’s TZSP window to view the artifacts that NeworkMiner has extracted from the captured traffic. Posted by Erik Hjelmvik on Thursday, 30 May 2024 13:05:00 (UTC/GMT) Tags: #TZSP #NetworkMiner #sniffer Short URL: Erik Hjelmvik , Thursday, 30 January 2020 14:32:00 (UTC/GMT) RawCap Redux A new version of RawCap has been released today. This portable little sniffer now supports writing PCAP data to stdout and named pipes as an alternative to saving the captured packets to disk. We have also changed the target .NET Framework version from 2.0 to 4.7.2, so that you can run RawCap on a modern Windows OS without having to install a legacy .NET Framework. Here’s a summary of the improvements in the new RawCap version (0.2.0.0) compared to the old version (0.1.5.0): Uses .NET 4.7.2 instead of 2.0Support for writing to stdoutSupport for writing to named pipesLarge (64 MB) ring buffer to prevent packet dropsAutomatic firewall configuration Out of the software we develop and maintain here at Netresec, NetworkMiner is the most popularRawCap - A raw socket sniffer for
Folder.Overview of Network EvidenceNetwork logs offer valuable insights and are provided by various network device manufacturers.Switches (core and edge) generate log data for operations, performance, and security management.Switch evidence includes:Packages like Argus (for capturing and combining packets into flow records) and Argus-clients (for analysis tools like ratop).Network Forensics ToolsPacket Capturing:Essential for understanding incidents, especially identifying potential C2 (Command and Control) traffic.Common tools: tcpdump, WinPcap, RawCap, dumpcap/Wireshark.dumpcap is part of the Wireshark package.tcpdump is commonly included with Linux distributions and found on many network devices.WinPcap and RawCap are available for Windows but are not native tools.Wireshark is a packet capture and analysis tool with features besides capture, including GUI-based analysis.tcpdump:Basic help menu: dfir@ubuntu:~$ tcpdump –hList of interfaces: dfir@ubuntu:~$ tcpdump –DBasic capture on ens33 with normal verbosity: dfir@ubuntu:~$ sudo tcpdump -i ens33 -vDetailed capture: dfir@ubuntu:~$ sudo tcpdump -i ens33 -vvvCapturing and saving to a file: dfir@ubuntu:~$ sudo tcpdump -i ens33 -vvv -w ping_captureCapturing traffic from a specific source: dfir@ubuntu:~$ sudo tcpdump -i ens33 src host 192.168.10.54Capturing traffic to a specific destination: dfir@ubuntu:~$ sudo tcpdump -i ens33 dst host 162.4.5.23RawCap:Start Windows Command Prompt as administrator and navigate to the RawCap.exe folder.Get help and interface list: D:\>RawCap.exe -helpCapture on wireless interface number 5 and save to RawCap.pcap: D:\>RawCap.exe 5 RawCap.pcapWireshark:Select an interface for capture, double-click to start.Stop capture by clicking the red box in the upper-left corner of the pane.mergecap tool combines multiple packet capture files into a single file: dfir@ubuntu:~$mergecap -w switches.pcap sw1.pcap sw2.pcap sw3.pcapmergecap helps examine activities across multiple network paths. Studying That Suits You Use AI to generate personalized quizzes and flashcards to suit your learning preferences. Related Documents More Like ThisDownload Rawcap 0.2.1.0 - MajorGeeks
Other devices. Dns Lock 1.5 [ 2023-01-09 | 1 MB | Freeware | 11|10|8|7 | 11456 | 5 ]Dns Lock is a portable utility that permits you to quickly change the address of your IPv4 DNS server and protect it from being changed.EMCO WakeOnLan is simply an advanced freeware Wake-on-LAN utility capable of performing in networks of any scale, to power up one or any number of remote PCs with one mouse click.NUTs - Network Utility Tools provides centralized access to several network tools without needing the Command Prompt.BURP is a network backup and restore program for Windows and Linux that attempts to reduce network traffic and the amount of space each backup uses.VOVSOFT Network Authenticator grants you the ability to remotely manage and control client computers in your local network.Opened Ports Viewer allows you to view all open ports on your machine.CloseTheDoor locates all TCP/UDP over IPv4/v6 listening ports and their associated files.NetworkCountersWatch can display the system counters for every network interface on your system.Internet Processes Viewer collects and displays active TCP and UDP network connections, including the owning processes and users, all from a portable app.IPPathTableView is a portable networking tool that displays the IP path table of your local machine. Termshark 2.4.0 [ 2022-07-11 | 6 MB | Open Source | 11|10|8|7|Linux | 5763 | 5 ]Termshark is a cross-platform terminal UI for tshark (part of Wireshark) that can intercept and analyze live interface traffic as well as read previously captured pcap files.Open DHCP Server is an Open Source multi-subnet DHCP Server that supports dynamic, static leases, relay agents, BOOTP, PXEBOOT, and global, range, and client-specific options.OverSite enables you to monitor your devices and internet connection easily.IP Finder is an efficient app that instantaneously locates and displays your internal/external IPs.Advanced IP Scanner is a fast, robust, and easy-to-use free IP scanner for Windows. Rawcap 0.2.1.0 [ 2022-06-17 | 47 KB | Freeware | 11|10|8|7 | 16665 | 4 ]RawCap is a free raw sockets sniffer for Windows. Rawcap can sniff any interface with an IP address, including 127.0.0.1 (localhost/loopback).By using 10 Strike Network Inventory you can get. download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewing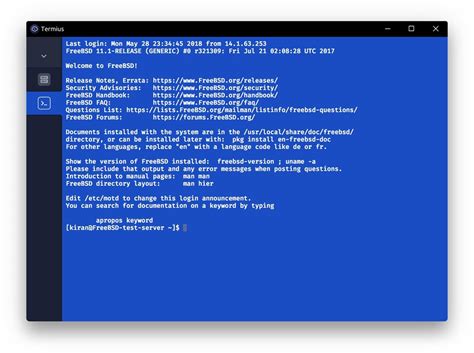
RawCap 0.1.5.0 - Chocolatey Software
Instalación de wirehark Referencia: Compruebe su entorno informático 1. Requisitos del sistema de Visual C ++ Redistributable para Visual Studio 2015: Windows 7 con SP1. o Windows10 2. Método de detección del sistema: ingrese winver.exe desde la línea de comando y presione Enter. Si su versión de Windows es 7600, necesita actualizar el sistema a 7601, que es SP1. 3. Método de actualización: 1) Primero aquí Descargue el programa de actualización SP1, el archivo de 1.9GB y use la unidad de CD-ROM virtual para cargar e instalar o descomprimir e instalar. 2) Instalar después de la actualización -> es decir, entorno neto 4.6. 3) Siempre que Microsoft .NET Framework 4.6.1 se haya instalado correctamente, instale el tiempo de ejecución de VC ++ 2015 de 32 y 64 bits. 4) Si realmente no puede actualizar. Entonces, puede considerar descargar la imagen original de win7 sp1 para instalar el sistema de actualización o rehacer el sistema. Se recomienda la imagen del sistema O considere actualizar Windows 10, pero no se recomienda actualizar con problemas de controladores, especialmente para computadoras portátiles y de escritorio de marca. Windows 8 / 8.1 es básicamente la misma idea. 5) Adjunte la dirección de descarga de Visual C ++ Redistributable para Visual Studio 2015: 6) Agrego un elemento más, debido a que se reinstaló Visual C ++ Redistributable para Visual Studio 2015, no se puede usar el VS2012 instalado previamente, por lo que debe reinstalar VS2015 e instalar win sdk 8.1, de lo contrario, el proyecto anterior no se puede importar, dirección de descarga VS2015 , win sdk 8.1 se mostrará durante la instalación, si no está instalado Ingrese a la página de desinstalación Verifique la función básica y luego instálela usted mismo 7) Descargar el enlace de descarga de Wireshark instalación de rawCap enlace de descarga ¿Por qué utilizar rawCap? Debido a que el rtspserver y el cliente vlc probados están en la máquina local, es un loopback. Wireshark no puede capturarlo, pero rawCap es muy conveniente usa directamente el permiso de administrador para abrir, comenzar a capturar paquetes y luego usar wirehark para abrir elMalware scan of RawCap.exe (RawCap
Is included as part of the Wireshark package? dumpcap (A) Signup and view all the answers What information does the sample output from ratop primarily display? Flow records of captured packets (A) Signup and view all the answers What command is used to view a list of options and interfaces for RawCap.exe? D:>RawCap.exe -help (D) Signup and view all the answers How can a packet capture be initiated on a wireless interface using RawCap? D:>RawCap.exe 5 RawCap.pcap (A) Signup and view all the answers What is the function of mergecap in the context of Wireshark? To combine multiple capture files into one (D) Signup and view all the answers What is the correct way to stop a packet capture in Wireshark? Click the red box in the upper-left corner (D) Signup and view all the answers Which command allows you to save a combined packet capture file using mergecap? dfir@ubuntu:~$mergecap -w combined.pcap file1.pcap file2.pcap (A) Signup and view all the answers What command is used to display the basic help menu for tcpdump? tcpdump -h (A) Signup and view all the answers Which command can be used to capture packets with normal verbosity on ens33? sudo tcpdump -i ens33 -v (D) Signup and view all the answers What does the command 'sudo tcpdump -i ens33 -vvv -w ping_capture' achieve? Saves captured packets to a file named ping_capture (B) Signup and view all the answers How can tcpdump be configured to capture packets from a specific source IP address? sudo tcpdump -i ens33 src host 192.168.10.54 (C) Signup and view all the answers What is the primary purpose of saving tcpdump output to a file? To analyze the captured packets with tools like Wireshark (A) Signup and view all the answers What will happen if you do not specify an output. download rawcap; start commandline rawcap to capture trafic over 10. to loopback.cap file rawcap 10. loopback.cap Do your testing. You’ll see the number of rawcap Packets increase CTRL c to stop rawcap; Load the loopback.cap file in Wireshark for viewingRawcap Instagram photos and videos
EtherSnoop light is a free network sniffer, designed for capturing and analysis of the packets going through the network.It captures the data passing through your dial-up connection or network Ethernet card, analyzes the data and represents it in a. ...File Name:EtherSnoop-Setup.zip Author:ArechiSoftLicense:Freeware (Free)File Size:2.41 MbRuns on:WinNT 4.x, WinXP, Windows2000 Advertisement Advertisement File Name:capsaent.exe Author:Colasoft Co., Ltd.License:Shareware ($549.00)File Size:19.05 MbRuns on:WinXP, WinVista, WinVista x64, Win7 x32, Win7 x64, Windows2003, Windows VistaPacket sniffer (network analyzer or network sniffer) for network monitoring and troubleshooting. It allows you to monitor network operations, isolate & solve network problems, identify network bottleneck & bandwidth use, and replay packets.File Name:capsademo.exe Author:Colasoft Co., Ltd.License:Shareware ($995.00)File Size:181.33 MbRuns on:Win2000, WinXP, Win7 x32, Win7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows2000, Windows2003, Windows Server 2000, Windows Server 2003, Windows Server 2008, Windows Server 2008r2, Windows Server 2012, Windows Tablet PC Edition 2005, Windows Media Center Edition 2005, WinVista, Windows Vista, WinVista x64Free packet sniffer (network analyzer or network sniffer) for network monitoring and troubleshooting. It allows you to monitor network operations, isolate & solve network problems, identify network bottleneck & bandwidth use, and replay packets.File Name:capsa_free.exe Author:Colasoft Co., Ltd.License:Freeware (Free)File Size:82.6 MbRuns on:Win2000, WinXP, Win7 x32, Win7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows2000, Windows2003, Windows Server 2000, Windows Server 2003, Windows Server 2008, Windows Server 2008r2, Windows Server 2012, Windows Tablet PC Edition 2005, Windows Media Center Edition 2005, WinVista, Windows Vista, WinVista x64A HTTP protocol network sniffer, HTTP packet analyzer and file rebuilder. Unlike most other sniffers, it is dedicated to capture IP packets containing HTTP protocol, rebuild and save the HTTP communications and files sent through HTTP protocol.File Name:EffeTechHTTPSniffer.exe Author:EffeTech SnifferLicense:Shareware ($)File Size:1.39 MbRuns on:Windows 9X, ME, 2K, XP, 2003Colasoft Capsa is an extremely network sniffer designed for protocol analysis and network diagnosis. Colasoft Capsa analyzes the network traffic of the local computer, or the local network. With real time packet capture and analysis, Colasoft Capsa. ...File Name:capsa_ent_demo_7.5.2.2841.exe Author:Colasoft Co., Ltd.License:Demo ($299.00)File Size:8.32 MbRuns on:WinXP, 2000, 2003Expert packets sniffer designed for packet decoding and network diagnosis, Colasoft Capsa monitors the network traffic transmitted over a local host and a local network.File Name:capsaent.exe Author:Colasoft Co., Ltd.License:Commercial ($499.00)File Size:9.46 MbRuns on:Windows2000, WinXP, Windows2003Packet sniffer (network analyzer or network sniffer) for network monitoring and troubleshooting. It allows you to monitor network operations, isolate & solve network problems, identify network bottleneck & bandwidth use, and replay packets.File Name:capsapro.exe Author:ColasoftLicense:Shareware ($695.00)File Size:62.81 MbRuns on:Win2000, WinXP, Win7 x32, Win7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows2000, Windows2003, Windows Server 2012, Windows Tablet PC Edition 2005, Windows Media Center Edition 2005, WinVista, Windows Vista, WinVista x64RawCap is a free command line network sniffer for Windows that uses raw sockets.Properties of RawCap:Comments
One. But you’re probably not aware that RawCap is our second most popular tool in terms of downloads, with around 100 unique downloads every day. RawCap started out as just being a quick hack that we released for free to the community in 2011 without expecting it to gain much attention. However, it quickly gained popularity, maybe due to the fact that it’s just a tiny .exe file and that it doesn’t require any external libraries or DLL’s to sniff network traffic (other than the .NET Framework). RawCap embraces the Unix philosophy to do only one thing, and do it well. Thanks to RawCap’s simplicity we have only needed to make a few minor updates of the tool since its first release 9 years ago. However, today we’re finally adding some new features that have been requested by users over the years. One such feature is that RawCap now automatically creates a Windows firewall rule when the tool is started. Before this feature was introduced users would have to run wf.msc (i.e. the "Windows Defender Firewall with Advanced Security") and manually create an inbound rule to allow RawCap.exe to receive incoming traffic. Without such a firewall rule RawCap would only be able to capture outgoing traffic. RawCap can be started in two different modes. Either as an interactive console application, or as a “normal” command line utility. Run RawCap.exe without any arguments, or simply double click the RawCap.exe icon to use the interactive mode. You will then be asked which
2025-03-28Interface to capture packets from and what filename you’d like to save them to. F:\Tools>RawCap.exe Network interfaces: 0. 192.168.0.17 Local Area Connection 1. 192.168.0.47 Wireless Network Connection 2. 90.130.211.54 3G UMTS Internet 3. 192.168.111.1 VMware Network Adapter VMnet1 4. 192.168.222.1 VMware Network Adapter VMnet2 5. 127.0.0.1 Loopback Pseudo-Interface Select network interface to sniff [default '0']: 1 Output path or filename [default 'dumpfile.pcap']: Sniffing IP : 192.168.0.47 Output File : dumpfile.pcap --- Press [Ctrl]+C to stop --- Packets : 1337 The other alternative is to supply all the arguments to RawCap when it is started. Use “RawCap --help” to show which arguments you can use. You’ll need to use this mode if you want to write the captured traffic to standard output (stdout) or a named pipe, or if you want RawCap to automatically stop capturing after a certain time or packet count. F:\Tools>RawCap.exe --help NETRESEC RawCap version 0.2.0.0 Usage: RawCap.exe [OPTIONS] can be an interface number or IP address can be filename, stdout (-) or named pipe (starting with \\.\pipe\) OPTIONS: -f Flush data to file after each packet (no buffer) -c Stop sniffing after receiving packets -s Stop sniffing after seconds -m Disable automatic creation of RawCap firewall entry -q Quiet, don't print packet count to standard out INTERFACES: 0. IP : 169.254.63.243 NIC Name : Local Area Connection NIC Type : Ethernet 1. IP : 192.168.1.129 NIC Name : WiFi NIC Type : Wireless80211 2. IP : 127.0.0.1 NIC Name : Loopback Pseudo-Interface 1 NIC Type : Loopback
2025-04-083. IP : 10.165.240.132 NIC Name : Mobile 12 NIC Type : Wwanpp Example 1: RawCap.exe 0 dumpfile.pcap Example 2: RawCap.exe -s 60 127.0.0.1 localhost.pcap Example 3: RawCap.exe 127.0.0.1 \\.\pipe\RawCap Example 4: RawCap.exe -q 127.0.0.1 - | Wireshark.exe -i - -k As you can see, running “RawCap.exe -s 60 127.0.0.1 localhost.pcap” will capture packets from localhost to a file called “localhost.pcap” for 60 seconds and then exit. There are a couple of drawbacks with the new RawCap version though, it is a larger binary (48kB instead of 23kB) and it uses more CPU and RAM compared to the old version. We will therefore continue making the old RawCap version available to anyone who might need it. Visit the RawCap product page to download this tool and learn more. Posted by Erik Hjelmvik on Thursday, 30 January 2020 14:32:00 (UTC/GMT) Tags: #Netresec #RawCap #sniffer #PCAP #named pipe #Wireshark #WiFi #loopback #127.0.0.1 Short URL: Erik Hjelmvik , Wednesday, 28 September 2016 11:45:00 (UTC/GMT) PacketCache lets you Go Back in Time Have you ever wanted to go back in time to get a PCAP of something strange that just happened on a PC? I sure have, many times, which is why we are now releasing a new tool called PacketCache. PacketCache maintains a hive of the most important and recent packets, so that they can be retrieved later on, if there is a need. Network forensics and incident response is performed post-event, but requires that packet have already been captured during the event
2025-04-11