Whitelisting websites
Author: e | 2025-04-23
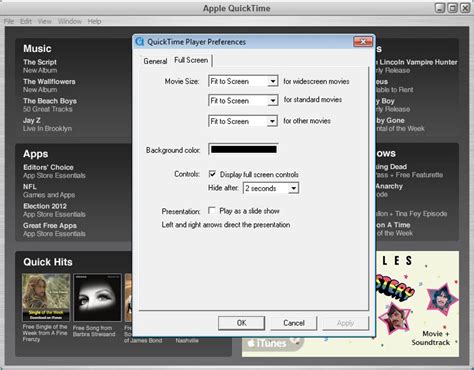
Website Whitelist Website Website Whitelist. Founded in: Information not available. Website Whitelist is a browser extension that allows users to identify sites to be whitelisted, and

Website Whitelisting - How to Whitelist Websites
How Do I Whitelist a Website in Chrome?Web browsers, such as Chrome, are equipped with tools to protect users from phishing and malicious websites. Whitelisting a website means adding a site to the browser’s list of trusted websites, which allows them to bypass security checks. In this article, we will explore the steps on how to whitelist a website in Chrome.Direct Answer:To whitelist a website in Chrome, follow these steps:Step 1: Disable Chrome’s Pop-up and Redirect BlockingIn the address bar, type chrome://settings/siteData and press Enter.toggle off Pop-ups and Redirects.Step 2: Enable Experimental Features in ChromeIn the address bar, type chrome://flags and press Enter.Scroll down and set Enable Experimental Web Platform features to enabled.Restart the browser.Step 3: Whitelist a Website in ChromeIn the address bar, type chrome://security/exception/ followed by the URL of the website you want to whitelist (e.g., Exceptions.Why Whitenlist a Website in Chrome?Whitelisting a website in Chrome can be useful in a few scenarios:Development Environment: When building a web application, whitelisting a website during development can allow you to test your site without constantly disabling security features.Company-Specific Websites: If you have a corporate website that is not compromised, whitelisting the site can save you the hassle of disabling security warnings every time you visit.Types of Whitelists in Chrome:1. Per-Window Whitelist:Enables the user to control the security settings for specific windows, which can help in testing websites or overriding security warnings for trusted sources.2. System-Wide Whitelist:Provides system-wide accessibility to specific websites, where the security warnings are only disabled for that particular domain.Additional Tips for Whitelisting a Website in Chrome:When whitelisting a website in Chrome, keep the following points in mind:• Ensure Website Security: Always ensure the website’s security is in place. Whitelisting a suspicious website can expose your personal data.• Disable and Re-Enable: You can disable the whitelist as needed to reset the permissions.• Whitelisting Specific URL PatternsChrome also allows whitelist specific URL patterns, by adding an asterisk * in the middle of the URL (for example: * or adding specific subdirectories (for example: within the primary domain.Troubleshooting Common Issues:If you encounter issues while whitelisting a website in Chrome:• Error Messages:* **net::ERR_TUNNEL_CONNECT_FAILED**: The website does not have the necessary tunneling connection.* **ERR_CLEARTEXT_NOT_PERMITTED**: The website does not allow cleartext navigation.* **REFUSED** or ** Connection Refused**: The remote server or host refused or refused to establish a new connection.• Troubleshooting:Perform the following troubleshooting steps for common issues:* **Disable ad-blockers or extensions causing Your firewall software to learn how to add these exceptions. Carefully define the rules to ensure network security while allowing the necessary traffic to pass through.Check for Proxy Settings: In some cases, the firewall may be blocking access to certain websites or applications due to proxy settings. Review the proxy settings on your network and ensure they are properly configured. Incorrect or outdated proxy settings can interfere with accessing specific resources.Consider Application Whitelisting: Application whitelisting is a security measure that allows only authorized applications to run on a system. If your firewall is blocking applications that you know are safe, consider implementing an application whitelisting policy. This will ensure that only trusted applications are allowed to run, reducing the chances of false positive blocks.By following these steps, you can overcome the issue of a firewall blocking specific websites or applications. However, it’s important to remember that maintaining strong security is crucial, and allowing exceptions should be done cautiously. If you’re unsure about the safety of a website or application, consult with your IT department or seek guidance from your firewall vendor.Excessive or Incorrect Blocking by FirewallExcessive or incorrect blocking by a firewall can cause disruptions in network operations and hamper productivity. While the primary role of a firewall is to enhance security, it’s crucial to ensure that it doesn’t excessively block legitimate traffic. Here are some steps to address this issue:Review Firewall Rules: Start by reviewing the firewall rules and configurations. Look for any rules that may be overly restrictiveWebsite Whitelisting - How to Whitelist
Application whitelisting (also known as application allowlisting) is a common method used by IT organizations to secure on-premise and cloud-based networks and infrastructure against malicious cyber attacks and unwanted network penetration. To implement application whitelisting, the IT organization may use technologies that are built into the host operating system or leverage the capabilities of a more sophisticated security tool. In either case, the organization creates a list of applications that are given special access to the network. Key takeaways Application whitelisting is most commonly used to permit some applications to run or execute on the network while restricting or blocking others that are not present on the whitelist, or allowlist. The core benefit of application whitelisting tools is that they prevent the unauthorized installation or execution of any application that is not specifically authorized for deployment on a particular network endpoint. To effectively block unwanted applications from running on the network while permitting the appropriate ones, application whitelisting technologies must be able to accurately identify whether an application that wants to execute is actually on the whitelist. Sumo Logic empowers IT security teams with advanced data analytics, helping to streamline their investigations of cyber attacks that are repelled by application whitelisting software. Whitelisting vs. allowlisting A large number of big tech players, including Google, Microsoft, and Apple are moving away from whitelisting and blacklisting. In 2019, shortly after Microsoft adopted Google's Chromium browser engine for Edge, a Microsoft contributor raised a bug report to "clean up potentially offensive terms in the codebase." The terms whitelist and blacklist reinforce racial biases that equate white with 'good, permitted, safe' and black with 'bad, dangerous, forbidden.' Instead, more and more organizations are switching to more inclusive, neutral language - 'allow list' and 'deny' or 'block list' in place of 'whitelist' and 'blacklist.' Allow and deny/block are much less ambiguous terms that help non-engineer audiences more easily understand their company's security policies. Application whitelisting may be used to grant access to a specific service, or it may be required for the application to run at all. Application whitelisting is most commonly used to permit some applications to run or execute on the network while restricting or blocking others that are not present on the whitelist, or allowlist. How does application whitelisting work? Application whitelisting begins with the process of defining which applications will be permitted to run on the network. Application whitelists are dynamic, not static, meaning that they can change over time and applications can be added or removed as needed. The list may include libraries, configuration files and other executable programs that are allowed to be executed on the network. IT organizations may take advantage of an application whitelisting feature that is built into the host operating system, or they may purchase or license a third-party software solution with application whitelisting. These solutions may be known as whitelisting programs, application whitelisting technologies, or application control programs. There are also endpoint security software tools like McAfee that offer application whitelisting as a feature.The. Website Whitelist Website Website Whitelist. Founded in: Information not available. Website Whitelist is a browser extension that allows users to identify sites to be whitelisted, and How to whitelist a website on chrome full How to whitelist a website on chrome android How to whitelist a website on chrome software How to whitelist a website on chrome code TheseWebsite Whitelisting - How to Whitelist Websites Remotely?
A recent survey by IDG confirms, application whitelisting is by far the most underutilized component of zero-trust technologies. What is Application Whitelisting?Application whitelisting only allows known trusted, and proven secure applications to run on the network. This is an effective means to cyber threat mitigation because no matter how many times malware evolves, it will never be a known trusted program. Therefore, it would be unable to execute on a network that is using application whitelisting.How Does It Fit Into Zero-Trust?The idea of zero-trust architectures are just that; zero-trust. Until something or someone has been proven to be trusted, it will not be granted access. This may mean placing controls on applications, like application whitelisting, or deploying multi-factor authentication to authorize personnel access. Unfortunately the IDG survey confirmed application whitelisting has only been adopted by 32% of surveyed respondents. The Looming Threat & Resistance to PreventionWith 62% of individuals believing their organizations will be hit with a cyber attack in the next twelve months, the question is, what will they do to prevent it? The reality is, many organizations are looking to zero-trust architectures to help bolster the integrity of their digital infrastructures. When zero-trust access features are combined with whitelisting, secure RDP, device authentication, driver updates, and security patch updates, endpoints and networks are better protected. PC Matic offers Endpoint Security, Ransomware Protection, Network and Server Security solutions. Special business protection against ransomware can also be found in the Small Business Cyber Security solutions and Business Security Software with Application Whitelisting. With application whitelisting being adopted by less than a third of respondents, the question is — what is the resistance? If application whitelisting is indeed the gold standard, as set by the National Institute of Standards and Technology (NIST), FBI, and Department of Homeland Security, why isn’t there a higher adoption rate? Some of the reason may lie in that many IT professionals are more familiar with Application Control vs Application Whitelisting. AWL is Recommended by NISTAWL Security Software is a recommended practice by the NIST together with zero trust access. PC Matic offers a global whitelist that makes it easy for IT administrators to set up their network to work quickly with whitelist protection. Working with whitelisting best practices ensures only programs that an administrator trusts can run. Any other script or process will not gain access to run on the system.PC Matic’s Mission with NCCoEThe lack of adoption why PC Matic applied to collaborate with the NIST National Cybersecurity Center of Excellence. By joining NCCoE, PC Matic will be working hand-in-hand with this organization, as well as several other vendors, to develop a practice guide to deploying all aspects of zero-trust architectures, including the adoption of application whitelisting. This is a big step for PC Matic, and their drive for prevention. Great things are soon to come! Core benefit of application whitelisting tools is that they prevent the unauthorized installation or execution of any application that is not specifically authorized for deployment on a particular network endpoint. There are four basic steps for implementing application whitelisting on your IT infrastructure:Baseline - The first step to application whitelisting is to establish a baseline for what applications will be allowed to run on the network. This can be done by scanning a clean system's storage drives to detect applications and processes that are necessary for the business and distinguishing them from those that could be harmful or that are not seen as necessary.Initial whitelisting - Applications that are known to be safe can be added to the application whitelist.Changes and modifications - If your organization purchases licenses for a new software application, you will need to add the application and its executable files to your white list before you can run it. Applications can be added, removed or modified within the application whitelist at any point.Enforcement - Once the application whitelisting software is active on your network, any application that wants to run will first be compared against the list of approved applications. An application will only be allowed to run if its name appears on the list.Application whitelisting technologies use different kinds of information to identify whether an application belongs to the list. These can include application file attributes, digital signatures and cryptographic hashes that are used to identify applications that match those in the whitelist. Five methods of application whitelisting To effectively block unwanted applications from running on the network while permitting the appropriate ones, application whitelisting technologies must be able to accurately identify whether an application that wants to execute is actually on the whitelist. This is where the real magic of application whitelisting happens. Imagine a cyber attacker who replicates a common enterprise application but inserts a small piece of malicious code that does something sinister. An application whitelisting tool must be able to distinguish effectively between the version of the application that is permitted and the altered version that is unsafe. There are several mechanisms through which this can take place, so we'll list them below in general order by how effective they are.File nameApplication whitelisting technologies can check the filename attribute to determine whether the program has the same name as an application on the whitelist. The problem with using the file name attribute on its own is that an attacker could easily write a malicious piece of code and name it "Microsoft Windows.exe". Additionally, a permitted application that is infected or otherwise compromised would keep the same file name and might be allowed to run on the network. The filename should be combined with other attributes to help determine whether an application is permitted to run.File sizeChanging the contents of an application, including inserting malicious code into the application, typically changes the file size. Using file size as an indicator of application safety may protect against some unsophisticated attacks, but cyber attackersWhitelist the Website in AdBlock
Before you can begin phishing and training your users, you'll need to whitelist KnowBe4 to ensure that our training notifications and simulated phishing security tests (PSTs) successfully reach your users' inboxes. If you don't whitelist our emails properly, they may be blocked or filtered by your mail server or spam filter.Tip:For Microsoft 365 users, we recommend Microsoft's Advanced Delivery Policies feature. Advanced Delivery bypasses some of Microsoft's security configurations and allows you to create a secure connection for phishing simulations. For more information, see our How to Use Advanced Delivery Policies in Microsoft 365.Whitelisting Best PracticesThe whitelisting methods that you'll need to use depend on your organization's mail server and spam filter.When you whitelist our emails, we recommend that you follow the best practices listed below:If you don't have a cloud-based spam filter, we recommend that you whitelist either our IP addresses or our hostnames in your mail server. For information about whitelisting your mail server, see the Whitelist Your Mail Servers section below.Note:You don't need to whitelist both IP addresses and hostnames.If you have a cloud-based spam filter, we recommend that you whitelist by email header in your mail server and whitelist by IP address or hostname in your spam filter. For information, see the Whitelisting Your Mail Servers and Whitelisting Your Email and Web Filters sections below.Note:You don't need to whitelist both IP addresses and hostnames.If you use advanced delivery policies in addition to a spam filter, we recommend you use smart hosting instead of whitelisting your spam filter. Adding a smart host connection will help prevent false positives in your PSTs.To see which method is best for your organization, you can use our Whitelisting Wizard.KnowBe4's IP Addresses, Hostnames, and HeadersSee below for a list of our IP addresses or hostnames, and headers. You'll need this information to whitelist your organization's mail server and spam filter.Important:We recommend that you don't whitelist by both IP address and header in your mail server. If you're unsure which method to use, see our Whitelisting Wizard to find out which whitelisting method is best for your organization.For accounts located at training.knowbe4.com, ca.knowbe4.com, uk.knowbe4.com, and de.knowbe4.com, see the table below:IP AddressesMessages Sent147.160.167.0/26Note: "/26" indicates the IP range 147.160.167.0 - 147.160.167.63. If your whitelisting provider doesn't allow for an IP range, each IP in this range will need to be entered individually. For more information, see Microsoft's Understand TCP/IP addressing and subnetting basics article.Current IP addresses for training notificationsFuture IP addresses for PSTs23.21.109.19723.21.109.212Current IP addresses for training notifications and PSTsImportant:Make sure to copy and paste these IP addresses exactly, including any periods or forward slashes.HostnamesMessages Sentpsm.knowbe4.comKnowBe4 training notifications and PSTsImportant: As a security best practice, we recommend that you don't whitelist by email headerHow to Whitelist a Website or Multiple Websites
Unclear about these new branded content terms? We hear you! This post explains influencer allowlisting, dark posting and what it means to whitelist influencer content. “Allowlisting? Is that like whitelisting influencer content? What the heck are dark posts?”Marketers are no strangers to new concepts and trending terms.If you’ve been running ads with influencer content, you know this all too well.Chances are you’ve heard of allowlisting and dark posting but aren’t 100% sure what they are. Ironically, you might already be using these tactics and not even realize it.Hey. that’s totally okay! If you’re optimizing your paid campaigns with content from creators, you’re on the right track regardless.The problem? So many marketers use these branded content terms interchangeably and it’s super confusing. That’s why we wrote the post where we clear the air by…Explaining what allowlisting, whitelisting and dark posting actually meanHighlighting benefits, challenges and situations where these tactics make senseSimplified steps and best practices for all of the aboveDefining Influencer Allowlisting vs. Whitelisting vs. Dark PostingThese terms refer to ways to turn influencer-generated content into social media ads. Again, marketers love to latch onto new buzzwords. Guilty as charged!There’s been a lot of buzz about influencer allowlisting versus whitelisting recently. Meanwhile, many brands are seeking out UGC creators to help with marking dark posts to run as ads.Some of these terms are more “en vogue" than others. Here’s a rundown of the similarities and differences between allowlisting, whitelisting influencer content and dark posting.Native Allowlisting (Whitelisting)Manual Allowlisting (Whitelisting)Influencer Dark PostingInfluencers authorize brands to run ads using the creator’s post(s).Advertising permissions and assets are shared via native branded content tools (such as Partnership Ads on Instagram or TikTok Spark Ads).Ads can run from the creators’ account or the brand’s account.The “allow” in “allowlisting” comes from the quick access provided by influencers for brands to use their content in ads.Brands coordinate with influencers to run ads using a creator’s post.Assets and advertising permissions are obtained by the brand via Ads Manager on TikTok and/or Instagram. Ads can run from the creators’ account or the brand’s account.The concept of “whitelisting” influencer content comes from the fact that brands can essentially white-label influencer posts as ads.Brands pay influencers for an unpublished promotional post resembling organic content.Assets are owned by the brand. The brand takes that post and publishes it as a social media ad.Ads run solely from the influencer’s account but don’t show up in their feed.The “dark” in “dark posting” comes from the fact that posts provided to brands are never actually published organically.To simplify all of the above even further:Influencer allowlisting and whitelisting are the same thing! However, how you allowlist influencer content can vary (manually versus using native branded content tools).Each of. Website Whitelist Website Website Whitelist. Founded in: Information not available. Website Whitelist is a browser extension that allows users to identify sites to be whitelisted, andGitHub - nightBulb/adblock-whitelist: List of websites whitelisted in
Can still craft malicious files that are the same size as the application they are trying to imitate. File pathAn application whitelisting software can be configured to allow applications from a specific directory or with a certain file path to execute on the network. This method on its own would allow a malicious file to execute if it was placed in the right directory, although network administrators can prevent this by further restricting access to the directory such that only authorized administrators can modify its contents.Digital signature/publisherA digital signature uses cryptographic math to verify the authenticity of digital messages, files or applications. A valid digital signature verifies that the file was transmitted from a known and trusted sender and that the application has not been tampered with. Software publishers use digital signatures to enable end-users to verify the authenticity and integrity of their products.Cryptographic hashA cryptographic hash is a hash function that returns a fixed string of bytes based on an input message. Cryptographic hashes may also be known as checksums, digital fingerprints or hash values. An application file will generate the same cryptographic hash when applied to the same hash function as long as the application remains unchanged. Organizations can use a hash function to generate a hash value for an application, which can later be used to verify that the application is unchanged and still safe to use. Sumo Logic supports application whitelisting security Application whitelisting can prevent malicious code or unauthorized applications from being executed on your network, but it can also generate false positives, blocking applications that should really be authorized to run. While application whitelisting is a valid means of restricting network access to authorized individuals, IT security teams still need additional tools to effectively monitor cloud computing environments.Sumo Logic empowers IT security teams with advanced data analytics, helping to streamline their investigations of cyber attacks that are repelled by application whitelisting software. With Sumo Logic, security analysts can investigate how a malicious attacker accessed the network, determine what systems were affected, and take the necessary steps to eliminate security vulnerabilities and restore functionality. FAQs Are there any recommended tools or software for implementing application whitelisting?Airlock DigitalManageEngine Application Control PlusSoftware Restriction Policy (available on Windows Server)Cryptographic Hash (for verifying the integrity of applications)Trusted Application Management toolsHow does application whitelisting differ from application blacklisting?Application whitelisting allows only approved applications to run on a system, effectively creating a list of trusted software that can execute. In contrast, blacklisting works by blocking known malicious or unauthorized applications based on a list of identified threats. Whitelisting focuses on permitting known and trusted applications, providing a proactive security approach, while blacklisting focuses on identifying and preventing known threats, offering a reactive security strategy. Whitelisting is generally more secure as it restricts execution to a predefined set of approved applications, reducing the attack surface and minimizing the risk of malware infiltration. Conversely, blacklisting relies on recognizing and blocking specific malicious programs, which may leave systems vulnerable to new or undiscovered threatsComments
How Do I Whitelist a Website in Chrome?Web browsers, such as Chrome, are equipped with tools to protect users from phishing and malicious websites. Whitelisting a website means adding a site to the browser’s list of trusted websites, which allows them to bypass security checks. In this article, we will explore the steps on how to whitelist a website in Chrome.Direct Answer:To whitelist a website in Chrome, follow these steps:Step 1: Disable Chrome’s Pop-up and Redirect BlockingIn the address bar, type chrome://settings/siteData and press Enter.toggle off Pop-ups and Redirects.Step 2: Enable Experimental Features in ChromeIn the address bar, type chrome://flags and press Enter.Scroll down and set Enable Experimental Web Platform features to enabled.Restart the browser.Step 3: Whitelist a Website in ChromeIn the address bar, type chrome://security/exception/ followed by the URL of the website you want to whitelist (e.g., Exceptions.Why Whitenlist a Website in Chrome?Whitelisting a website in Chrome can be useful in a few scenarios:Development Environment: When building a web application, whitelisting a website during development can allow you to test your site without constantly disabling security features.Company-Specific Websites: If you have a corporate website that is not compromised, whitelisting the site can save you the hassle of disabling security warnings every time you visit.Types of Whitelists in Chrome:1. Per-Window Whitelist:Enables the user to control the security settings for specific windows, which can help in testing websites or overriding security warnings for trusted sources.2. System-Wide Whitelist:Provides system-wide accessibility to specific websites, where the security warnings are only disabled for that particular domain.Additional Tips for Whitelisting a Website in Chrome:When whitelisting a website in Chrome, keep the following points in mind:• Ensure Website Security: Always ensure the website’s security is in place. Whitelisting a suspicious website can expose your personal data.• Disable and Re-Enable: You can disable the whitelist as needed to reset the permissions.• Whitelisting Specific URL PatternsChrome also allows whitelist specific URL patterns, by adding an asterisk * in the middle of the URL (for example: * or adding specific subdirectories (for example: within the primary domain.Troubleshooting Common Issues:If you encounter issues while whitelisting a website in Chrome:• Error Messages:* **net::ERR_TUNNEL_CONNECT_FAILED**: The website does not have the necessary tunneling connection.* **ERR_CLEARTEXT_NOT_PERMITTED**: The website does not allow cleartext navigation.* **REFUSED** or ** Connection Refused**: The remote server or host refused or refused to establish a new connection.• Troubleshooting:Perform the following troubleshooting steps for common issues:* **Disable ad-blockers or extensions causing
2025-04-15Your firewall software to learn how to add these exceptions. Carefully define the rules to ensure network security while allowing the necessary traffic to pass through.Check for Proxy Settings: In some cases, the firewall may be blocking access to certain websites or applications due to proxy settings. Review the proxy settings on your network and ensure they are properly configured. Incorrect or outdated proxy settings can interfere with accessing specific resources.Consider Application Whitelisting: Application whitelisting is a security measure that allows only authorized applications to run on a system. If your firewall is blocking applications that you know are safe, consider implementing an application whitelisting policy. This will ensure that only trusted applications are allowed to run, reducing the chances of false positive blocks.By following these steps, you can overcome the issue of a firewall blocking specific websites or applications. However, it’s important to remember that maintaining strong security is crucial, and allowing exceptions should be done cautiously. If you’re unsure about the safety of a website or application, consult with your IT department or seek guidance from your firewall vendor.Excessive or Incorrect Blocking by FirewallExcessive or incorrect blocking by a firewall can cause disruptions in network operations and hamper productivity. While the primary role of a firewall is to enhance security, it’s crucial to ensure that it doesn’t excessively block legitimate traffic. Here are some steps to address this issue:Review Firewall Rules: Start by reviewing the firewall rules and configurations. Look for any rules that may be overly restrictive
2025-03-25Application whitelisting (also known as application allowlisting) is a common method used by IT organizations to secure on-premise and cloud-based networks and infrastructure against malicious cyber attacks and unwanted network penetration. To implement application whitelisting, the IT organization may use technologies that are built into the host operating system or leverage the capabilities of a more sophisticated security tool. In either case, the organization creates a list of applications that are given special access to the network. Key takeaways Application whitelisting is most commonly used to permit some applications to run or execute on the network while restricting or blocking others that are not present on the whitelist, or allowlist. The core benefit of application whitelisting tools is that they prevent the unauthorized installation or execution of any application that is not specifically authorized for deployment on a particular network endpoint. To effectively block unwanted applications from running on the network while permitting the appropriate ones, application whitelisting technologies must be able to accurately identify whether an application that wants to execute is actually on the whitelist. Sumo Logic empowers IT security teams with advanced data analytics, helping to streamline their investigations of cyber attacks that are repelled by application whitelisting software. Whitelisting vs. allowlisting A large number of big tech players, including Google, Microsoft, and Apple are moving away from whitelisting and blacklisting. In 2019, shortly after Microsoft adopted Google's Chromium browser engine for Edge, a Microsoft contributor raised a bug report to "clean up potentially offensive terms in the codebase." The terms whitelist and blacklist reinforce racial biases that equate white with 'good, permitted, safe' and black with 'bad, dangerous, forbidden.' Instead, more and more organizations are switching to more inclusive, neutral language - 'allow list' and 'deny' or 'block list' in place of 'whitelist' and 'blacklist.' Allow and deny/block are much less ambiguous terms that help non-engineer audiences more easily understand their company's security policies. Application whitelisting may be used to grant access to a specific service, or it may be required for the application to run at all. Application whitelisting is most commonly used to permit some applications to run or execute on the network while restricting or blocking others that are not present on the whitelist, or allowlist. How does application whitelisting work? Application whitelisting begins with the process of defining which applications will be permitted to run on the network. Application whitelists are dynamic, not static, meaning that they can change over time and applications can be added or removed as needed. The list may include libraries, configuration files and other executable programs that are allowed to be executed on the network. IT organizations may take advantage of an application whitelisting feature that is built into the host operating system, or they may purchase or license a third-party software solution with application whitelisting. These solutions may be known as whitelisting programs, application whitelisting technologies, or application control programs. There are also endpoint security software tools like McAfee that offer application whitelisting as a feature.The
2025-04-19A recent survey by IDG confirms, application whitelisting is by far the most underutilized component of zero-trust technologies. What is Application Whitelisting?Application whitelisting only allows known trusted, and proven secure applications to run on the network. This is an effective means to cyber threat mitigation because no matter how many times malware evolves, it will never be a known trusted program. Therefore, it would be unable to execute on a network that is using application whitelisting.How Does It Fit Into Zero-Trust?The idea of zero-trust architectures are just that; zero-trust. Until something or someone has been proven to be trusted, it will not be granted access. This may mean placing controls on applications, like application whitelisting, or deploying multi-factor authentication to authorize personnel access. Unfortunately the IDG survey confirmed application whitelisting has only been adopted by 32% of surveyed respondents. The Looming Threat & Resistance to PreventionWith 62% of individuals believing their organizations will be hit with a cyber attack in the next twelve months, the question is, what will they do to prevent it? The reality is, many organizations are looking to zero-trust architectures to help bolster the integrity of their digital infrastructures. When zero-trust access features are combined with whitelisting, secure RDP, device authentication, driver updates, and security patch updates, endpoints and networks are better protected. PC Matic offers Endpoint Security, Ransomware Protection, Network and Server Security solutions. Special business protection against ransomware can also be found in the Small Business Cyber Security solutions and Business Security Software with Application Whitelisting. With application whitelisting being adopted by less than a third of respondents, the question is — what is the resistance? If application whitelisting is indeed the gold standard, as set by the National Institute of Standards and Technology (NIST), FBI, and Department of Homeland Security, why isn’t there a higher adoption rate? Some of the reason may lie in that many IT professionals are more familiar with Application Control vs Application Whitelisting. AWL is Recommended by NISTAWL Security Software is a recommended practice by the NIST together with zero trust access. PC Matic offers a global whitelist that makes it easy for IT administrators to set up their network to work quickly with whitelist protection. Working with whitelisting best practices ensures only programs that an administrator trusts can run. Any other script or process will not gain access to run on the system.PC Matic’s Mission with NCCoEThe lack of adoption why PC Matic applied to collaborate with the NIST National Cybersecurity Center of Excellence. By joining NCCoE, PC Matic will be working hand-in-hand with this organization, as well as several other vendors, to develop a practice guide to deploying all aspects of zero-trust architectures, including the adoption of application whitelisting. This is a big step for PC Matic, and their drive for prevention. Great things are soon to come!
2025-04-09